67% of consumers today say they don’t understand how companies use their personal data, and 73% feel they have little…
As manufacturers of perimeter security appliances, including CCTV systems, firewalls, radar systems, access control devices, motion sensors, and similar products,…
As cyber threats continue to evolve, organizations are increasingly turning to innovative technologies to bolster their cybersecurity defenses. One of…
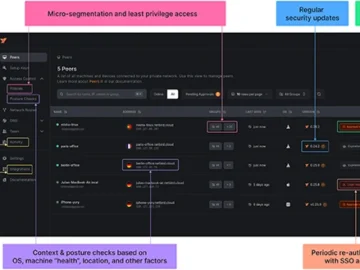
NetBird is an open-source solution that integrates a configuration-free peer-to-peer private network with centralized access control, providing a single platform…
Australian authorities are doubling up on technical assistance requests sent to cloud and network service providers because the laws prevent…
As cyberattacks surge, businesses face unprecedented pressure to fortify defenses. Simultaneously, governments are tightening regulations to combat evolving threats, turning…
Cybersecurity is a high-stakes, high-pressure field in which CISOs and their teams constantly battle threats, compliance requirements, and business expectations….
Mar 12, 2025Ravie LakshmananEndpoint Security / Vulnerability Apple on Tuesday released a security update to address a zero-day flaw that…
Microsoft today issued more than 50 security updates for its various Windows operating systems, including fixes for a whopping six…
The notorious Lazarus Group, a North Korean state-backed hacking group, is back at it again. This time, they’re sneaking malicious…
Datacentre developers should be doing more to ensure local communities are reaping the full benefits that having a server farm…
Apple fixed the third actively exploited zero-day of 2025 Pierluigi Paganini March 11, 2025 Apple addressed a zero-day vulnerability, tracked…