PowerSchool has published a long-awaited CrowdStrike investigation into its massive December 2024 data breach, which determined that the company was previously…
The social network X suffered intermittent outages on Monday, a situation owner Elon Musk attributed to a “massive cyberattack.” Musk…
Fake Elon Musk endorsements are used in SMS campaigns to sell bogus energy-saving devices. Learn how to spot these scams…
Despite the increasing efforts to increase women’s representation in cybersecurity, the industry still has a long way to go. However, there…
Mar 11, 2025Ravie LakshmananNetwork Security / Vulnerability Unpatched TP-Link Archer routers have become the target of a new botnet campaign…
Pure Storage has announced FlashBlade//Exa, which aims at artificial intelligence (AI) and high-performance computing (HPC) workloads that demand extremely high…
CISA warned U.S. federal agencies to secure their networks against attacks exploiting three critical vulnerabilities affecting Ivanti Endpoint Manager (EPM)…
A Proof-of-Concept (PoC) has been released for a significant vulnerability discovered in SolarWinds Web Help Desk, exposing encrypted passwords and…
Mar 11, 2025The Hacker NewsBreach Simulation / Penetration Testing In cybersecurity, confidence is a double-edged sword. Organizations often operate under…
The Post Office has made interim compensation offers to a number of former subpostmasters affected by a major data breach…
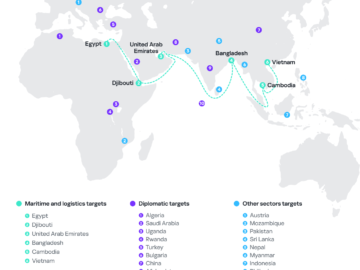
SideWinder APT targets maritime and nuclear sectors with enhanced toolset Pierluigi Paganini March 11, 2025 The APT group SideWinder targets…
The SideWinder Advanced Persistent Threat (APT) group has been observed intensifying its activities, particularly targeting military and government entities across…