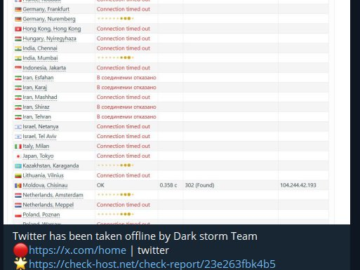
Elon Musk blames a massive cyberattack for the X outages Pierluigi Paganini March 10, 2025 Elon Musk said that the…
Apple has taken another step toward the official release of iOS 18.4 by seeding the third developer beta of the…
EncryptHub, a rising cybercriminal entity, has been under scrutiny by multiple threat intelligence teams, including Outpost24’s KrakenLabs. Recent investigations have…
The telecom industry is at a major turning point. With 5G, IoT, and AI reshaping global connectivity, the need for…
Security researchers have identified a sophisticated attack campaign attributed to APT37, a North Korean state-sponsored hacking group also known as…
Ragnar Loader, a sophisticated toolkit associated with the Ragnar Locker ransomware group, has been instrumental in facilitating targeted cyberattacks on…
International law enforcement disrupts Garantex, a multi-billion-dollar cryptocurrency exchange used for money laundering. Two individuals, Aleksej Besciokov and Aleksandr Mira…
TFE Hotels, which includes the Adina, Vibe and Travelodge brands, is recovering from a “cyber incident” disclosed earlier this month,…
Today CISA added three Ivanti Endpoint Manager (EPM) vulnerabilities CVE-2024-13159, CVE-2024-13160, and CVE-2024-13161 to its Known Exploited Vulnerabilities (KEV) catalog….
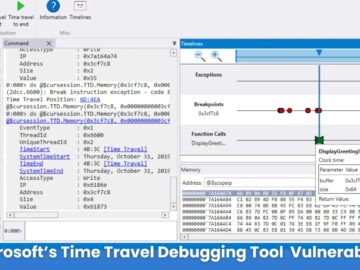
Microsoft’s Time Travel Debugging (TTD) framework, a powerful tool for recording and replaying Windows program executions, has been found to…
Digital bank Up has appointed Meera Shanaaz Aneez to the role of chief technology officer, as incumbent Chris Aitchison moves to…
CISA has likely added two VeraCore vulnerabilities, CVE-2024-57968 and CVE-2025-25181, to its Known Exploited Vulnerabilities (KEV) catalog due to active…