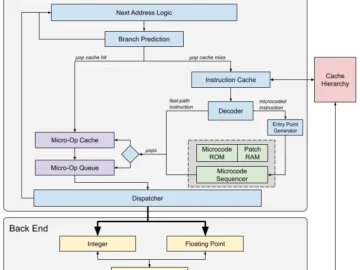
A recent vulnerability analysis made by the Google Bug Hunters team reveals an important flaw in the microcode signature validation…
Microsoft Threat Intelligence detected a large-scale malvertising campaign in early December 2024 that infected nearly one million devices globally in…
A series of significant security vulnerabilities have been discovered in the Thinkware Dashcam, specifically the F800 Pro model, which could…
The February Patch Tuesday updates and activity during the month marked a return to normalcy for patch management. Following the…
Commvault has revealed a major vulnerability in its software that could allow malicious actors to gain full control of its…
In today’s world, smartphones have evolved from luxury gadgets to essential tools that we rely on for a variety of…
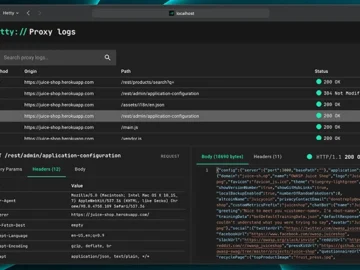
Hetty is an open-source HTTP toolkit designed for security research, offering a free alternative to commercial tools like Burp Suite…
The Apache Software Foundation has disclosed several vulnerabilities affecting its Traffic Server software. These vulnerabilities allow malicious actors to exploit…
In today’s hyper-connected world, the Internet of Things (IoT) and digital technologies have revolutionized industries across the globe. However, with…
Every year, millions of old tech are thrown away due to age, malfunctions, or to make way for new ones,…
A significant vulnerability has been uncovered in the Python JSON Logger package (python-json-logger), affecting versions 3.2.0 and 3.2.1. This flaw,…
Mar 10, 2025Ravie LakshmananThreat Intelligence / Cybercrime A new mass malware campaign is infecting users with a cryptocurrency miner named…