Microsoft has launched Microsoft 365 E5 Security as an add-on to its Business Premium suite, providing small and medium-sized businesses…
Mar 07, 2025Ravie LakshmananCryptocurrency / Ransomware A coalition of international law enforcement agencies has seized the website associated with the…
GitHub has unveiled groundbreaking applications of its AI-powered coding assistant, Copilot, specifically tailored for security professionals analyzing system logs and…
GitHub Copilot, once a developer-centric tool, is now revolutionizing workflows across technical and non-technical roles. With features like Agent Mode,…
Mar 07, 2025Ravie LakshmananMalware / Blockchain Cybersecurity researchers have discovered a malicious Python package on the Python Package Index (PyPI)…
The Federal Bureau of Investigation (FBI) has alerted businesses about a disturbing new data extortion scam targeting corporate executives. The…
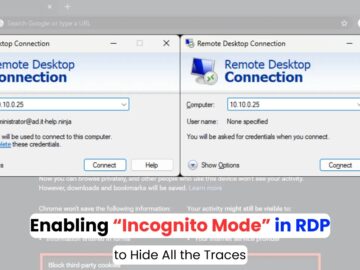
Microsoft’s Remote Desktop Protocol (RDP) has introduced a lesser-known but critical security feature colloquially referred to as “incognito mode” through…
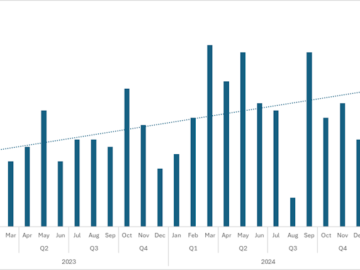
Medusa ransomware attacks have seen a significant increase, rising by 42% between 2023 and 2024, with a further escalation in…
Medusa Ransomware targeted over 40 organizations in 2025 Pierluigi Paganini March 07, 2025 Medusa ransomware has claimed nearly 400 victims…
Cybersecurity research firm NISOS has uncovered a network of suspected North Korean IT workers who are leveraging GitHub to create…
A critical security flaw (CVE-2024-56325) in Apache Pinot, a real-time distributed OLAP datastore, has been disclosed, allowing unauthenticated attackers to…
Security researchers have uncovered a critical vulnerability in AMD Zen CPUs that allows attackers with elevated privileges to load malicious…