Elastic has released a critical security update to address a vulnerability in Kibana, a widely used data visualization and analysis…
Traditional training often lacks the hands-on experience cybersecurity teams need to counter advanced threats. AI-powered gamified simulations combine artificial intelligence…
Mar 07, 2025Ravie LakshmananSecurity Breach / Cryptocurrency Safe{Wallet} has revealed that the cybersecurity incident that led to the Bybit $1.5…
Over the years, ransomware attacks have followed a predictable pattern, with cybercriminal groups displaying ransom notes on the screens of…
Mar 07, 2025Ravie LakshmananThreat Intelligence /Vulnerability Threat actors of unknown provenance have been attributed to a malicious campaign predominantly targeting…
The near universal strategy of migrating corporate applications to the cloud has left many companies in a hybrid middle state,…
Here’s a look at the most interesting products from the past week, featuring releases from Outpost24, Palo Alto Networks, Red…
Commonwealth Bank is expecting to complete its data migration to AWS by May this year, cutting an 18-month project by…
A newly identified vulnerability in the Cisco Secure Client for Windows could allow attackers to execute arbitrary code with SYSTEM…
Qilin Ransomware gang claims the hack of the Ministry of Foreign Affairs of Ukraine Pierluigi Paganini March 07, 2025 Qilin…
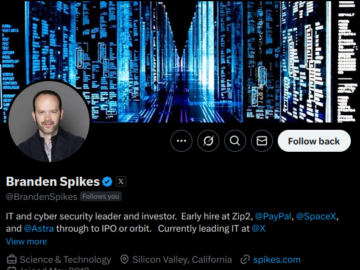
At 49, Branden Spikes isn’t just one of the oldest technologists who has been involved in Elon Musk’s Department of…
A large-scale cybercrime operation dubbed “PrintSteal” has been exposed, revealing a complex network involved in the mass production and distribution…