The National Health Service (NHS) has long been plagued by cybersecurity controversies, with one of the most notable incidents being…
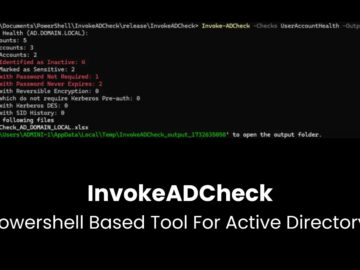
Securing Active Directory (AD) is a critical priority for organizations. Misconfigurations in AD, such as excessive permissions, outdated protocols, or…
In a major coordinated operation, several U.S. law enforcement agencies have charged 12 Chinese nationals with a series of cyber…
MillionPodcasts, who calls itself the ultimate destination for podcast media contacts, recently released a list of the best 100 cybercrime podcasts….
Removing 24 malicious apps from the Google Play store and silencing some servers almost halved a botnet known as BadBox….
Mar 06, 2025Ravie LakshmananThreat Intelligence / Vulnerability The threat actors behind the Medusa ransomware have claimed nearly 400 victims since…
Dive Brief: Cyberattacks targeting third-party vendors are causing more financial damage than ever before, cyber risk management firm Resilience said…
A newly devised “polymorphic” attack allows malicious Chrome extensions to morph into browser extensions, including password managers, crypto wallets, and banking…
Security researchers at SEC Consult have discovered a significant vulnerability in CrowdStrike’s Falcon Sensor that allowed attackers to bypass detection…
The United States Army is employing a prototype generative artificial intelligence tool to identify references to diversity, equity, inclusion, and…
Palo Alto, Singapore, March 6th, 2025, CyberNewsWire With recent attack disclosures like Browser Syncjacking and extension infostealers, browser extensions have…
Palo Alto, Singapore, March 6th, 2025, CyberNewsWire With recent attack disclosures like Browser Syncjacking and extension infostealers, browser extensions have…