Carding — the underground business of stealing, selling and swiping stolen payment card data — has long been the dominion…
A significant vulnerability has been identified in large language models (LLMs) such as ChatGPT, raising concerns over their susceptibility to…
Q: Tell us about your role at Snap and why cybersecurity is vital to your business. Jim Higgins: I’m Snap’s…
The Chinese APT hacking group “Mustang Panda” has been spotted abusing the Microsoft Application Virtualization Injector utility as a LOLBIN to…
A recent study by researchers from the National University of Singapore and NCS Cyber Special Ops R&D explores how the…
Two critical OpenSSH vulnerabilities discovered! Qualys TRU finds client and server flaws (CVE-2025-26465 & CVE-2025-26466) enabling MITM and DoS. Upgrade…
OpenSSH has released security updates addressing two vulnerabilities, a machine-in-the-middle (MitM) and a denial of service flaw, with one of…
A sophisticated malware campaign was launched by cybercriminals, targeting users through trojanized versions of popular games. Exploiting the holiday season’s…
Feb 18, 2025Ravie LakshmananVulnerability / Network Security Two security vulnerabilities have been discovered in the OpenSSH secure networking utility suite…
Until now, IT leaders have needed to consider the cyber security risks posed by allowing users to access large language…
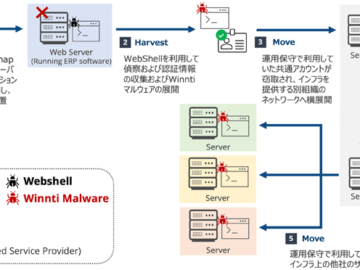
China-linked APT group Winnti targets Japanese organizations since March 2024 Pierluigi Paganini February 18, 2025 China-linked threat actor Winnti targeted…
Over the past 8 months, Luke (hakluke) Stephens and I have spoken with 10 security executives, surveyed over 550 security professionals,…