Many companies from a range of industries worldwide are stuck at a trial stage of emerging technologies usage, according to…
Microsoft warns Apple developers about a new XCSSET malware variant targeting macOS, posing security risks through stealthy infections and data…
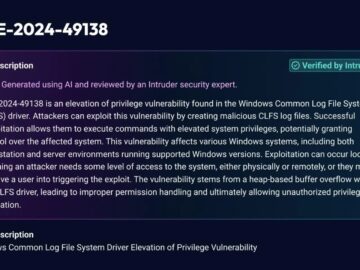
Intel by Intruder now uses AI to contextualize NVD descriptions, helping security teams assess risk faster. Intruder, a leader in…
Intel by Intruder now uses AI to contextualize NVD descriptions, helping security teams assess risk faster. Intruder, a leader in…
Intel by Intruder now uses AI to contextualize NVD descriptions, helping security teams assess risk faster. Intruder, a leader in…
Data loss is becoming a bigger danger for businesses, both financially and numerically. According to an IBM report, the average data…
Feb 18, 2025Ravie LakshmananThreat Intelligence / Malware Cybersecurity researchers are alerting to a new campaign that leverages web injects to…
A newly created public-private partnership looks set to oversee the creation of the world’s largest artificial intelligence (AI) datacentre in…
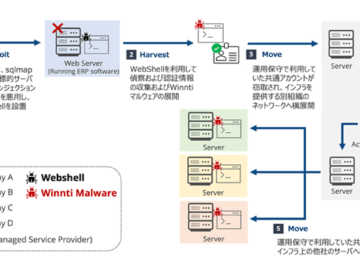
Feb 18, 2025Ravie LakshmananMalware / Network Security The China-linked threat actor known as Winnti has been attributed to a new…
The CrowdStrike incident in 2024 hit the UK like a hurricane. As it swept across the country, it ground flights…
Newspaper publishing giant Lee Enterprises has confirmed that a ransomware attack is behind ongoing disruptions impacting the group’s operations for…
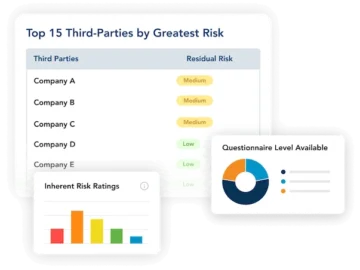
ProcessUnity announced the next generation of the Global Risk Exchange. This platform transforms the third-party assessment process, reducing friction for…