Insurance group IAG is trialling Starlink “micro terminals” to enable property assessors to work in weather-affected or natural disaster zones….
People throw the term “AGI” around like it’s nothing, but they rarely define what they mean by it. So most…
A formal ban on the use of Kaspersky Lab software by the federal government last month was triggered by “a…
I have a strong intuition about how we’ll achieve both AGI and consciousness in machines. Keep in mind: it’s just…
The US Federal Bureau of Investigation (FBI) is probing a cyberattack at Oracle that has led to the theft of…
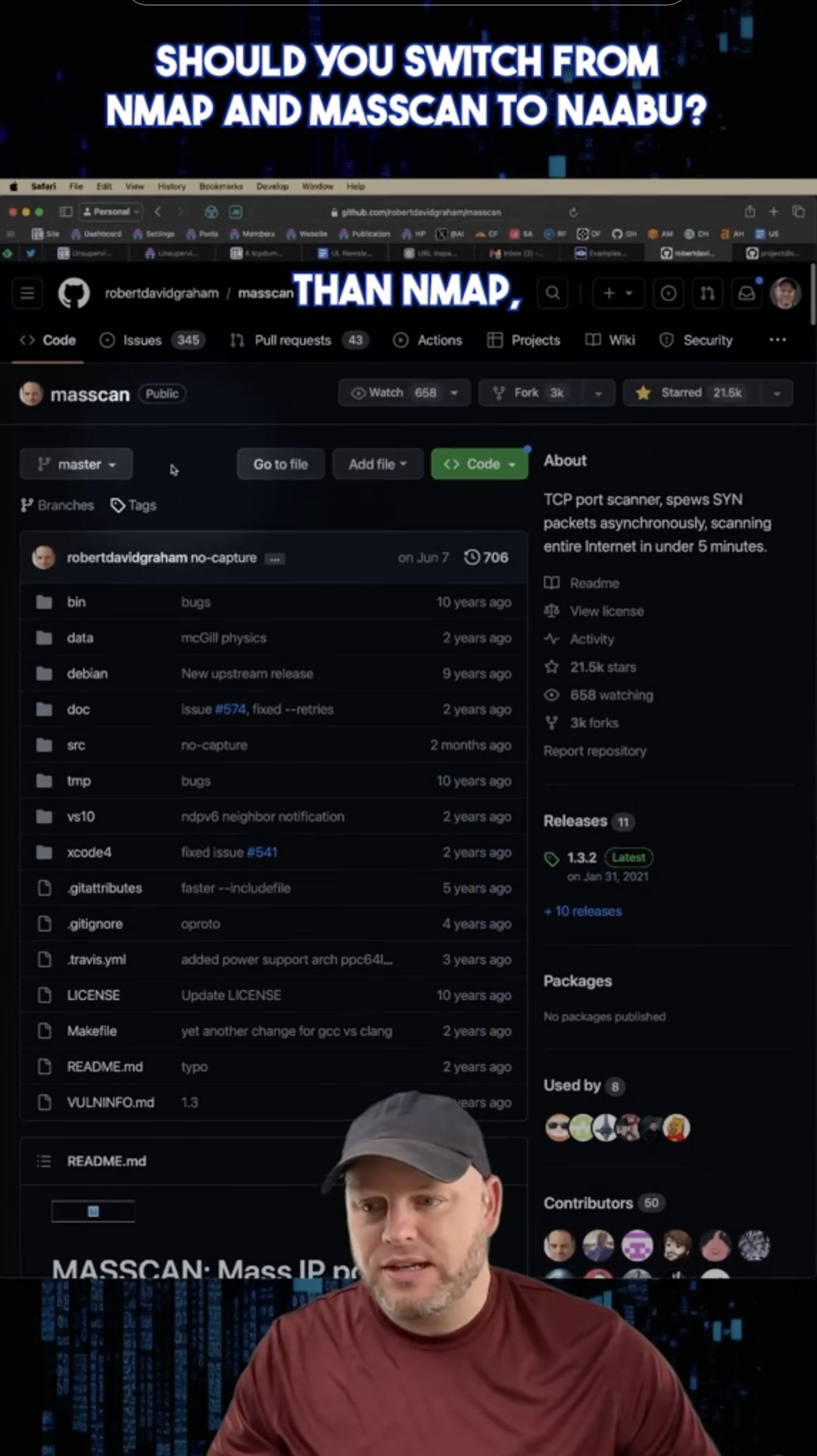
Naabu for the win This is my first short-form video. Kind of random what I did for the first topic,…
AARNet will take over operation of telecommunications services on the Basslink cable linking Victoria and Tasmania from July. The internet…
Read more about AIL At least 10 times a month I find myself in a book and they make a…
UniSuper is starting to explore opportunities with agentic AI, with an initial use case aimed at helping a financial advisory…
I think I just figured out why so many people burn out in defensive cybersecurity after a decade or two….
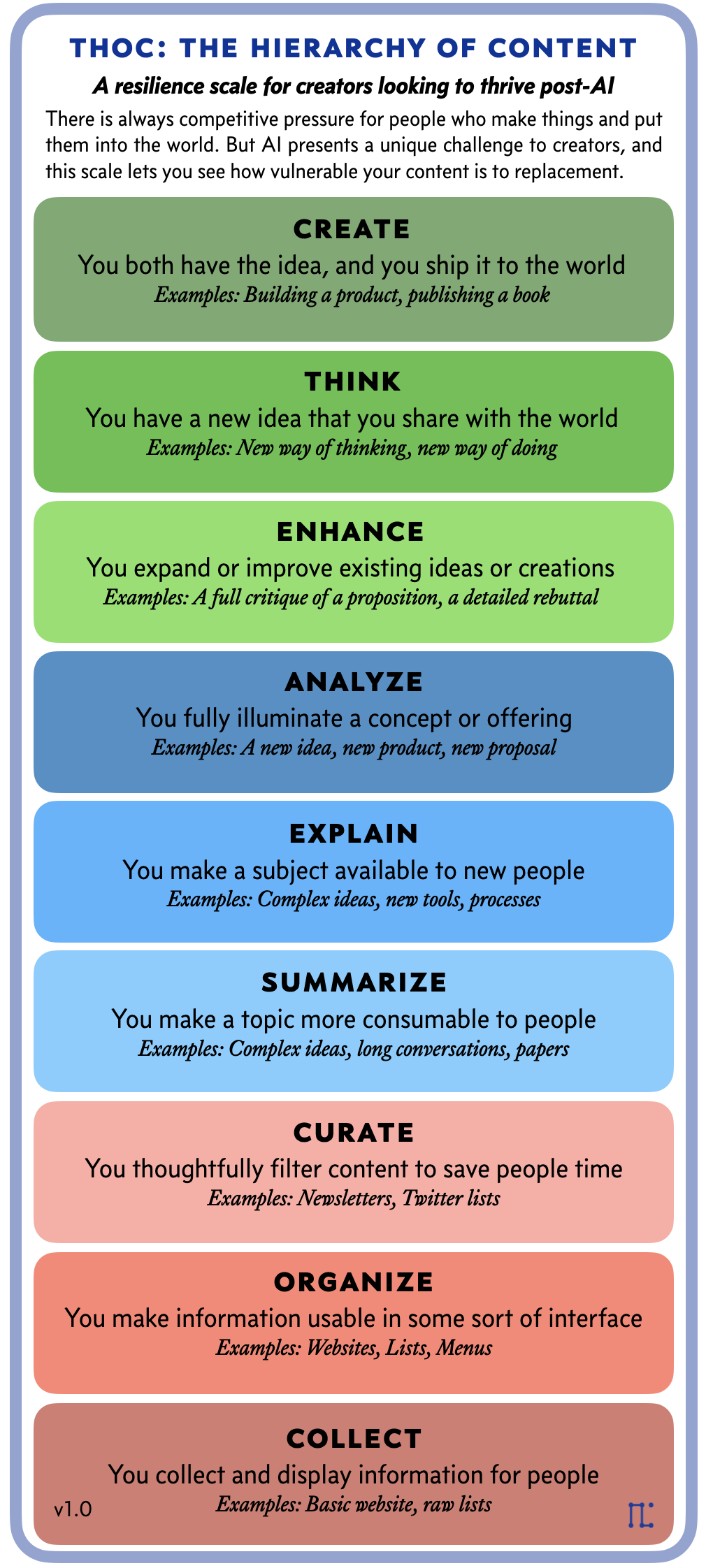
THOC — The Hierarchy of Content There are thousands of newsletters out there that hit you with the latest news,…
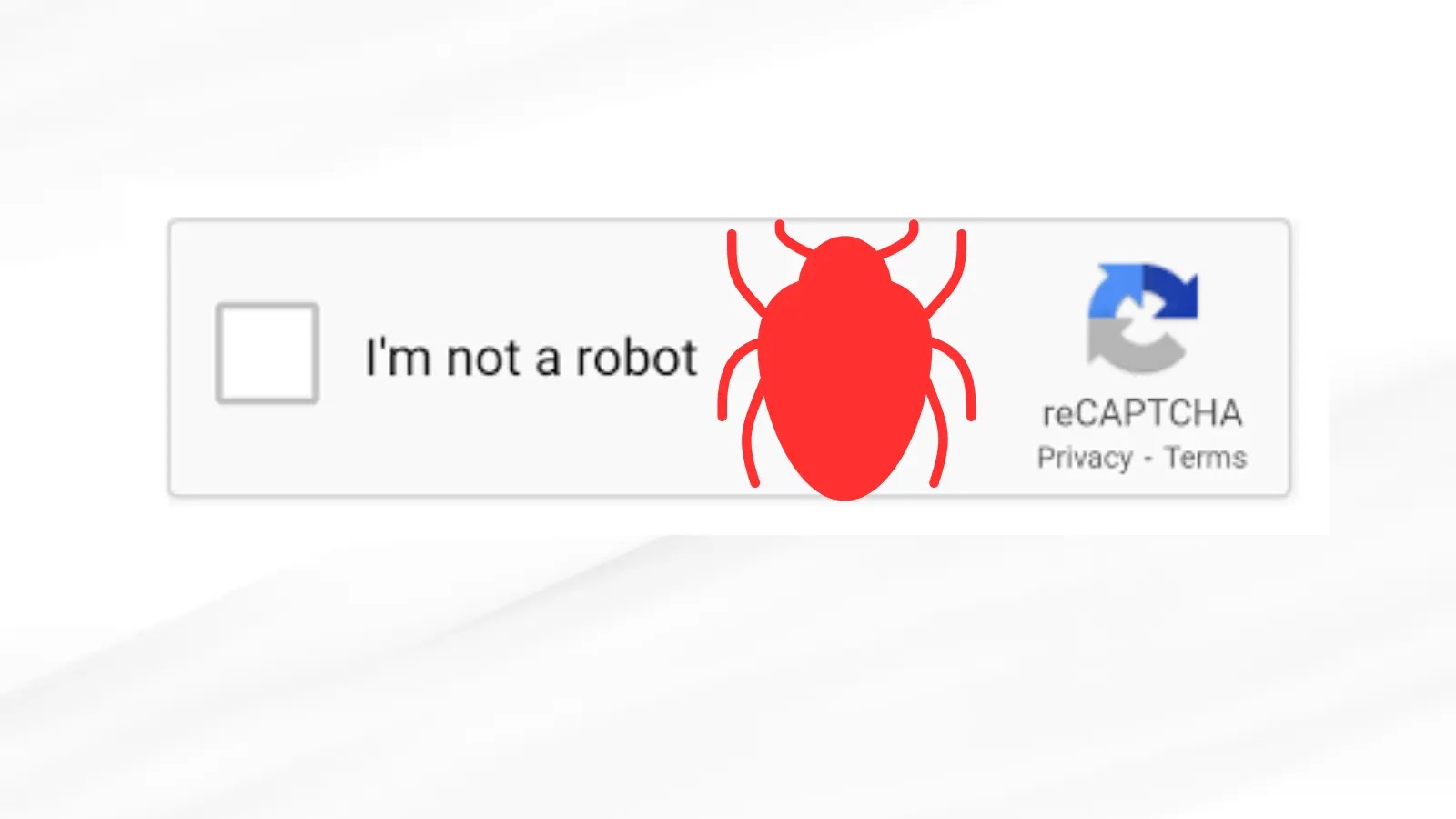
A sophisticated social engineering technique known as ClickFix has emerged, leveraging fake CAPTCHA verification processes to deceive users into executing…