The Cybersecurity and Infrastructure Security Agency has frozen all of its election security work and is reviewing everything it has…
U.S. CISA adds SimpleHelp flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini February 14, 2025 U.S. Cybersecurity and Infrastructure Security…
RansomHub emerges as a major ransomware threat in 2024, targeting 600 organizations after ALPHV and LockBit disruptions. Group-IB reveals its…
Hackers are launching attacks against Palo Alto Networks PAN-OS firewalls by exploiting a recently fixed vulnerability (CVE-2025-0108) that allows bypassing authentication….
Having served on the MITRE.org CVE (OVAL) advisory board, I have spent years analyzing vulnerabilities and how they impact global…
Cloud security remains an evolving challenge as new attack vectors emerge, often leveraging misconfigurations rather than outright software vulnerabilities. In…
Feb 14, 2025Ravie LakshmananVulnerability / DevOps Cybersecurity researchers have disclosed a new type of name confusion attack called whoAMI that…
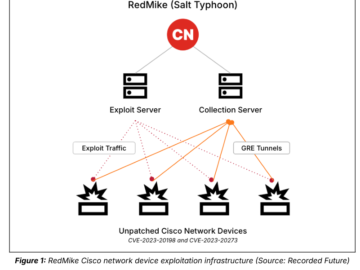
China-linked APT Salt Typhoon breached telecoms by exploiting Cisco router flaws Pierluigi Paganini February 14, 2025 China-linked APT Salt Typhoon…
A phishing attack dubbed DEEP#DRIVE is targeting South Korean entities, with thousands already affected. North Korean hackers from the Kimsuky…
Attackers are now targeting an authentication bypass vulnerability affecting SonicWall firewalls shortly after the release of proof-of-concept (PoC) exploit code….
A cybercriminal claimed to have stolen 15 million data records from the customers and clients of the company Zacks—a number…
Feb 14, 2025Ravie LakshmananBrowser Security / Cryptocurrency The North Korean threat actor known as the Lazarus Group has been linked…