QuSecure™, Inc., a leader in post-quantum cryptography (PQC) and cryptographic agility, has secured additional funding, bringing its Series A round…
14 Feb Empowering SOC Teams with Open and Seamless API Integration Posted at 11:53h in Blogs by Taylor Fox Boosting…
For years, cyber threat actors have been launching attacks to spread malware and deploy tools for intelligence gathering, often driven…
MetricStream has unveiled its annual forecast of key trends shaping the future of GRC and Cyber GRC. These 2025 predictions…
Over the years, we have witnessed numerous applications scanning smartphones for intelligence, extracting data, and transferring it to remote servers….
Organizations are continually balancing seamless user experiences and implementing robust defenses against evolving threats. Passwords, as the first line of…
Dafydd Stuttard | 14 February 2025 at 14:23 UTC AI is rapidly gaining traction in virtually every industry. But in…
Rapid7’s vulnerability research team says attackers exploited a PostgreSQL security flaw as a zero-day to breach the network of privileged…
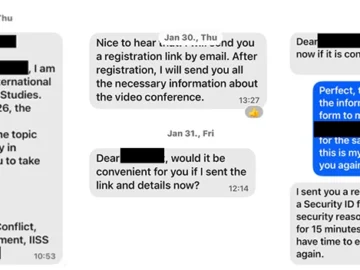
Suspected Russian threat actors have been taking advantage of Microsoft Device Code Authentication to trick targets into granting them access…
The government of Prime Minister Anthony Albanese has imposed additional cyber sanctions in response to a major 2022 cyberattack that…
Netwrix, a leading provider of cybersecurity solutions focused on data and identity threat protection, has introduced a new component to…
Around the world, security leaders say they are struggling to balance the need to appropriately secure their data and the…