Speed is everything in the modern business world. Our attention spans are shorter than ever, consumers demand short and seamless…
With incidences of ransomware on the rise, nobody should even be thinking that an attack is something that couldn’t happen…
China’s Salt Typhoon hackers are still actively targeting telecoms worldwide and have breached more U.S. telecommunications providers via unpatched Cisco…
A newly discovered vulnerability in Microsoft Windows, identified by ClearSky Cyber Security, is reportedly being actively exploited by the Chinese…
For years, cybersecurity training programs have been stuck in the same rut: entertaining videos, knowledge-heavy lectures, and phishing tests that…
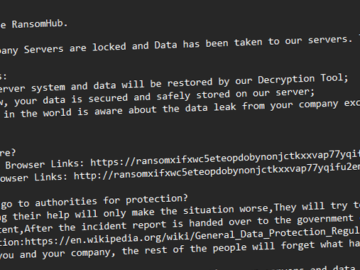
The threat actors behind the RansomHub ransomware-as-a-service (RaaS) scheme have been observed leveraging now-patched security flaws in Microsoft Active Directory…
The government has asked businesses for comment on a UK approach to electronic invoicing (e-invoicing), which is part of its…
NVIDIA has issued a critical security update to address a high-severity vulnerability discovered in the NVIDIA® Container Toolkit for Linux….
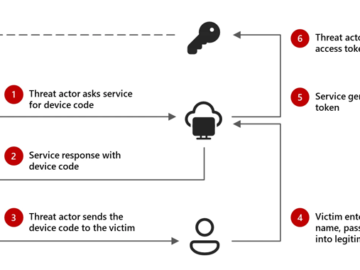
Feb 14, 2025Ravie LakshmananEnterprise Security / Cyber Attack Microsoft is calling attention to an emerging threat cluster it calls Storm-2372…
Microsoft has fixed a known issue causing “boot device inaccessible” errors during startup on some Windows Server 2025 systems using…
A newly discovered vulnerability in WinZip, a popular file compression and archiving utility, has raised alarms among cybersecurity experts. Identified…
Social engineering is advancing fast, at the speed of generative AI. This is offering bad actors multiple new tools and…