For years, cybersecurity training programs have been stuck in the same rut: entertaining videos, knowledge-heavy lectures, and phishing tests that…
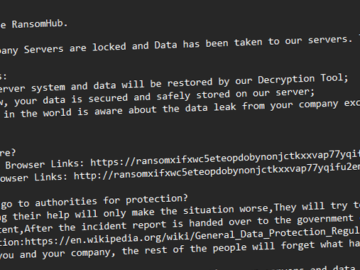
The threat actors behind the RansomHub ransomware-as-a-service (RaaS) scheme have been observed leveraging now-patched security flaws in Microsoft Active Directory…
The government has asked businesses for comment on a UK approach to electronic invoicing (e-invoicing), which is part of its…
NVIDIA has issued a critical security update to address a high-severity vulnerability discovered in the NVIDIA® Container Toolkit for Linux….
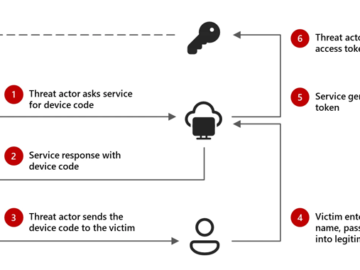
Feb 14, 2025Ravie LakshmananEnterprise Security / Cyber Attack Microsoft is calling attention to an emerging threat cluster it calls Storm-2372…
Microsoft has fixed a known issue causing “boot device inaccessible” errors during startup on some Windows Server 2025 systems using…
A newly discovered vulnerability in WinZip, a popular file compression and archiving utility, has raised alarms among cybersecurity experts. Identified…
Social engineering is advancing fast, at the speed of generative AI. This is offering bad actors multiple new tools and…
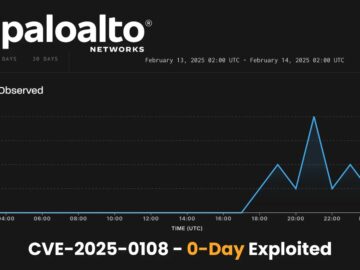
Palo Alto Networks has released a patch for a high-severity authentication bypass vulnerability, identified as CVE-2025-0108, affecting their PAN-OS software. GreyNoise…
Threat actors actively exploit a new high-severity vulnerability, CVE-2025-0108, in Palo Alto Networks’ PAN-OS. This exploit allows attackers to bypass…
A newly disclosed high-severity vulnerability in WinZip, tracked as CVE-2025-1240, enables remote attackers to execute arbitrary code on affected systems…
A sophisticated phishing campaign leveraging the device code authentication flow has been identified by Microsoft Threat Intelligence, targeting a wide…