Researchers have uncovered a high-severity SQL injection vulnerability, CVE-2025-1094, affecting PostgreSQL’s interactive terminal tool, psql. This flaw was identified during…
A new phishing kit named Astaroth has emerged as a significant threat in the cybersecurity landscape by bypassing two-factor authentication…
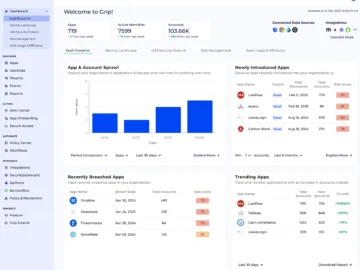
Grip Security has unveiled its SaaS Security Posture Management (SSPM) solution, which proactively identifies misconfigurations, enforces best practices and strengthens…
Researchers observed a sophisticated cyber-espionage campaign led by the Chinese state-sponsored group known as “Salt Typhoon,” also referred to as…
A security vulnerability has been identified in the AMD Ryzen™ Master Utility, a performance-tuning tool for AMD Ryzen™ processors. This flaw, discovered by a security researcher,…
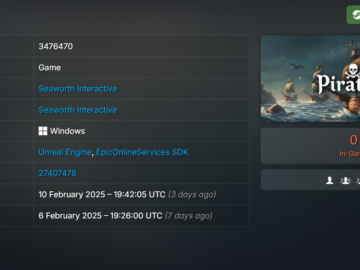
Valve removed the game PirateFi from the Steam video game platform because contained a malware Pierluigi Paganini February 14, 2025…
A high-severity security vulnerability, identified as CVE-2024-21966, has been discovered in the AMD Ryzen™ Master Utility, a software tool designed…
Dutch police and the Public Prosecution Service have taken down a network of 127 command-and-control servers. This network was operated…
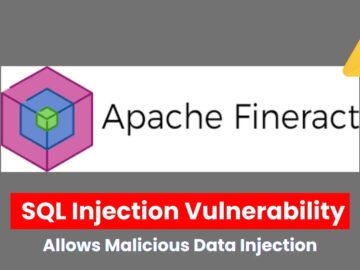
The Apache Software Foundation has disclosed a critical SQL injection vulnerability in its widely utilized financial platform, Apache Fineract. The…
2024 is set to be a record year for scammers who received at least US$9.9 billion in crypto revenues from…
Feb 14, 2025Ravie LakshmananZero-Day / Vulnerability Threat actors who were behind the exploitation of a zero-day vulnerability in BeyondTrust Privileged…
47% of organizations have experienced a data breach or cyberattack over the past 12 months that involved a third-party accessing…