This year, we launched new initiatives designed to bring people together in fun and innovative ways, including playing online games,…
UK telecommunications company TalkTalk is investigating a third-party supplier data breach after a threat actor began selling alleged customer data…
Many Facets, One Goal A common trope in cybersecurity is “don’t roll your own auth.” There’s a reason for this: implementing…
New York State has announced a $2,000,000 settlement with PayPal over charges it failed to comply with the state’s cybersecurity regulations,…
If you weren’t lucky enough to catch us at a roadshow event, you’ll be delighted to know you can catch…
Subaru Starlink flaw allowed experts to remotely hack cars Pierluigi Paganini January 25, 2025 Subaru Starlink flaw exposed vehicles and…
This blog will break down the NIS2 Directive drawing information from the original directive briefing published by the European Parliament…
Retail and e-commerce organizations are major targets this time of year, which is why proactive security testing is essential to…
UnitedHealth Group has confirmed that a ransomware attack targeted its subsidiary, Change Healthcare, in February 2024, impacting 190 million Americans….
Participants in the Pwn2Own Automotive 2025 earned $886,250 Pierluigi Paganini January 25, 2025 The Pwn2Own Automotive 2025 hacking contest has…
1. Are You Prepared to Manage Incoming Vulnerability Reports? Naturally, the purpose of running a bug bounty program is to…
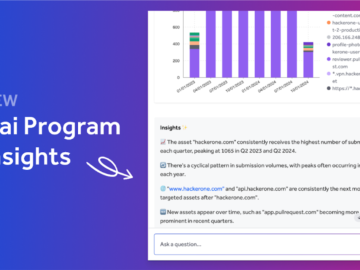
Transforming Security Program Management: A Day with Hai Picture this: It’s Monday morning, and your dashboard shows fifteen new vulnerability…


![How an MFA Bypass Led to Account Takeover [Plus 11 Authentication Tips] Hackerone logo](https://image.cybernoz.com/wp-content/uploads/2025/01/How-an-MFA-Bypass-Led-to-Account-Takeover-Plus-11-360x270.png)






![Is Your Security Ready For Bug Bounty? [5 Questions] Hackerone logo](https://image.cybernoz.com/wp-content/uploads/2025/01/Is-Your-Security-Ready-For-Bug-Bounty-5-Questions-360x270.png)