Arm Holdings plans to launch its own chip this year after securing Meta Platforms as one of its first customers,…
In 2024, a new hybrid cold war is redefining the threat landscape. Cyber, physical, and geopolitical risks are converging, with…
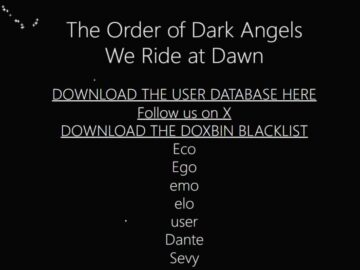
Doxbin Data Breach: Hackers leak 136,000+ user records, emails, and a ‘blacklist’ file, exposing those who paid to keep their…
Telstra has disabled external-facing access to a database used by some enterprise and wholesale customers to manage network settings and…
The Rise of Cyber Espionage: UAV and C-UAV Technologies as Targets Pierluigi Paganini February 13, 2025 Researchers at cybersecurity firm…
The Dutch Police (Politie) dismantled the ZServers/XHost bulletproof hosting operation after taking offline 127 servers used by the illegal platform. Earlier this…
An unprecedented letter from the US Congress, released today, accuses the UK of “a foreign cyberattack waged through political means”….
Over a hundred cyber security experts, companies and civil society groups have signed a letter calling for the Home Secretary,…
Zacks Investment Research (Zacks) last year reportedly suffered another data breach that exposed sensitive information related to roughly 12 million…
North Korean state-sponsored group Kimsuky (aka Emerald Sleet, aka VELVET CHOLLIMA) is attempting to deliver malware to South Korean targets…
Valentine’s Day 2025 is just around the corner, and many men are likely busy picking out thoughtful gifts to impress…
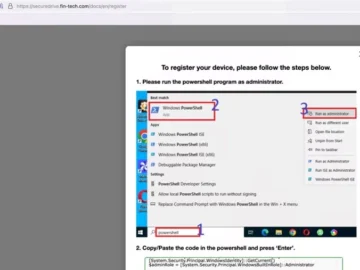
Feb 13, 2025Ravie LakshmananWeb Security / Cloud Security A widespread phishing campaign has been observed leveraging bogus PDF documents hosted…