As the European Union (EU) prepares to respond to Trump’s 25% tariff on aluminium and steel, a widely reported paper…
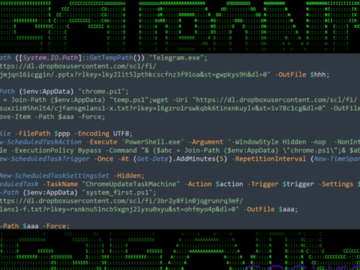
China-linked APTs’ tool employed in RA World Ransomware attack Pierluigi Paganini February 13, 2025 A November 2024 RA World ransomware…
Over half a billion websites are powered by WordPress as of today. Unfortunately, not every instance deserves the same security…
A China-based threat actor, tracked as Emperor Dragonfly and commonly associated with cybercriminal endeavors, has been observed using in a ransomware…
Introduction The mobile application landscape is more dynamic and challenging than ever, with businesses increasingly relying on mobile channels to…
New Astaroth Phishing Kit bypasses 2FA (two-factor authentication) to steal Gmail, Yahoo and Microsoft login credentials using a reverse proxy,…
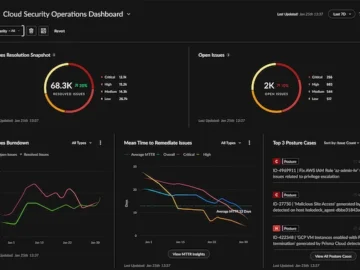
Palo Alto Networks introduced Cortex Cloud, the next version of Prisma Cloud, that natively brings together new releases of its…
Feb 13, 2025Ravie LakshmananUnited States A nation-state threat actor with ties to North Korea has been linked to an ongoing…
13 Feb Training Employees To Defend Against Ransomware Posted at 08:50h in Blogs by Taylor Fox This week in cybersecurity…
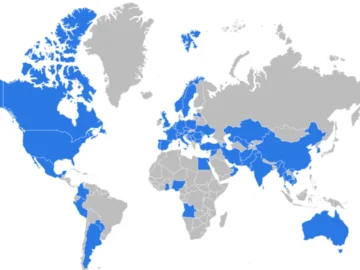
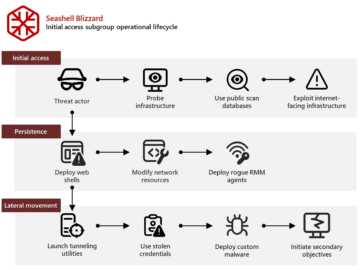
A subgroup of Russia’s Sandworm APT has been working to achieve initial and persistent access to the IT networks of…
AI is everywhere now, transforming how businesses operate and how users engage with apps, devices, and services. A lot of…
Russia-linked APT Seashell Blizzard is behind the long running global access operation BadPilot campaign Pierluigi Paganini February 13, 2025 A…