A recent analysis of over one million malware samples by Picus Security has revealed a growing trend in the exploitation…
Lee Enterprises, one of the largest newspaper groups in the United States, says a cyberattack that hit its systems caused…
In a significant breakthrough against global cybercrime, Thai authorities announced today the arrest of four European nationals linked to the…
The SHA256 algorithm, a cryptographic hash function, is widely used for securing data integrity and authenticity. It processes input data…
Today on the Lock and Code podcast… In February 2024, a 14-year-old boy from Orlando, Florida, committed suicide after confessing…
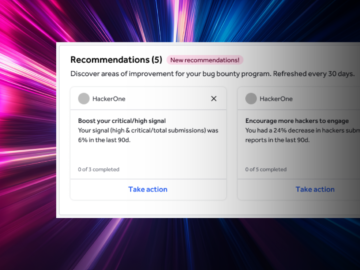
Meet HackerOne Recommendations: a built-in intelligence layer that continuously refines your security program, delivering personalized insights and your program’s historical performance….
A global law enforcement operation targeting the Phobos ransomware gang has led to the arrest of four suspected hackers in…
A critical security vulnerability, CVE-2024-52875, has been identified in GFI KerioControl firewalls, affecting versions 9.2.5 through 9.4.5. This flaw, which…
The infamous Handala hacking group, with suspected ties to Iranian intelligence, has claimed responsibility for a cyberattack against Israel’s police…
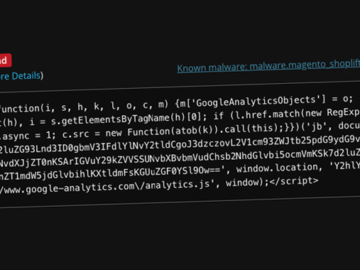
Feb 10, 2025Ravie LakshmananMalware / Payment Security Threat actors have been observed leveraging Google Tag Manager (GTM) to deliver credit…
When was the last time you checked DNS configurations for subdomains pointing at services not in use? According to Crowdsource…
A recent analysis of over 1 million malware samples unveiled a trend where adversaries increasingly exploit the Application Layer of…