Free Webinar – Supply Chain Attack Prevention Recent attacks like Polyfill[.]io show how compromised third-party components become backdoors for hackers….
The new year has started with a whirlwind of activity, and one of the hottest topics in the news is…
Feb 10, 2025Ravie LakshmananVulnerability / Malware Threat actors have been observed exploiting multiple security flaws in various software products, including…
Brave Browser is getting a new feature called ‘custom scriptlets’ that lets advanced users inject their own JavaScript into websites,…
Linus Torvalds announced the release of Linux Kernel 6.14-rc2, the second release candidate in the 6.14 series. The release follows…
Security validation has officially turned a corner. Once considered a “nice-to-have” it’s now a top priority for security leaders worldwide….
A newly discovered vulnerability in AnyDesk, the popular remote desktop software, has sparked serious cybersecurity concerns. Identified as CVE-2024-12754 and…
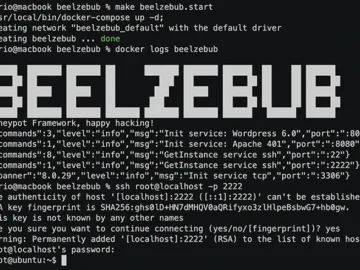
Beelzebub is an open-source honeypot framework engineered to create a secure environment for detecting and analyzing cyber threats. It features…
The government is inviting local and regional authorities across the country to bid to become one of the UK’s artificial…
Bunnings has analysed a decade’s worth of Australian weather data to help personalise its customer marketing and in-store merchandising efforts….
Sony said that all PlayStation Plus members would automatically receive an additional five days of service, after a global outage…
Meta Platforms plans to carry out its expected company-wide layoffs this week while pushing ahead with the expedited hiring of…