Mobile devices have become a prime target for financial fraud, as the availability of digital payments and interception of OTPs…
An online shop is more than just another way to sell your products. It comes with a responsibility to keep…
Feb 05, 2025Ravie LakshmananCryptocurrency / Data Breach The North Korea-linked Lazarus Group has been linked to an active campaign that…
U.S. CISA adds Microsoft .NET Framework, Apache OFBiz, and Paessler PRTG Network Monitor flaws to its Known Exploited Vulnerabilities catalog…
The Spanish police have arrested a suspected hacker in Alicante for allegedly conducting 40 cyberattacks targeting critical public and private organizations,…
In recent years, you’ve probably encountered numerous news stories about victims of ransomware attacks and the payments made to obtain…
Earlier this week, people attending OpenUK’s State of Open Con were presented with a vision of open government that has…
A 22-year-old Canadian man, Andean Medjedovic, is facing federal charges in the U.S. for allegedly exploiting smart contract vulnerabilities in…
Cybersecurity Ventures predicts that global cybercrime damages will reach $10.5 trillion annually by 2025. This staggering figure highlights the urgent need…
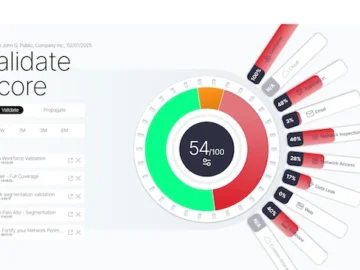
SafeBreach launched SafeBreach exposure validation platform, which combines the power of its time-tested breach and attack simulation (BAS) product—now called…
Feb 05, 2025Ravie LakshmananThreat Intelligence / Malware A previously undocumented threat actor known as Silent Lynx has been linked to…
Silver Spring, Maryland, February 5th, 2025, CyberNewsWire Aembit, the non-human identity and access management (IAM) company, today announced that Michael…