Amazon Web Services (AWS) and Microsoft have not taken kindly to the UK competition watchdog’s proposal to take a targeted…
The Cybersecurity and Infrastructure Security Agency (CISA) has recently updated its Known Exploited Vulnerabilities (KEV) Catalog by adding several new…
Iranian-linked threat group Sharp Boys allegedly hacked at least five Israeli hotel reservation sites. “This connection is not private. This…
Several critical vulnerabilities affecting Mali Graphics Processing Units (GPUs) have surfaced, allowing hackers to exploit flaws in GPU drivers to…
Defense Tech companies that seek to maximize their chances of winning government contracts must understand current and future cybersecurity requirements….
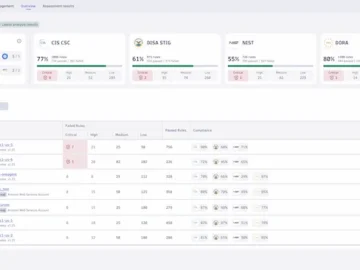
Dynatrace announced the expansion of its security portfolio with a new Cloud Security Posture Management (CSPM) solution. For enterprises managing…
ICAO and ACAO Breached: Cyberespionage Groups Targeting Aviation Safety Specialists Pierluigi Paganini February 05, 2025 The International Civil Aviation Organization…
In an impressive demonstration of cost-effective AI research, a group of researchers has successfully replicated DeepSeek’s R1-Zero model for just…
Deepfakes and stolen Personally Identifiable Information (PII) can be used for more than hoaxes, phishing, and identity theft. Now, these…
A sophisticated cyber espionage campaign attributed to the Chinese hacking group DaggerFly has been identified, targeting Linux systems through an…
The eSentire Threat Response Unit (TRU) revealed that threat actors are actively exploiting a six-year-old IIS vulnerability in Progress Telerik…
Given the tremendous growth in cyberattacks during the COVID pandemic, it may be tempting to assume that external threats must…