A critical security flaw, identified as CVE-2025-21298, has been disclosed in Microsoft’s Windows Object Linking and Embedding (OLE) technology. This…
SpyCloud, a leading identity threat protection company, has unveiled key innovations in its portfolio, driving a shift towards holistic identity…
Cybercrime is among the most significant threats to modern businesses—no matter the size of the company or its sector. With…
Feb 04, 2025Ravie LakshmananMalware / Cryptocurrency The North Korean threat actors behind the Contagious Interview campaign have been observed delivering…
Outgoing CISA chief Jen Easterly recently compared secure software development to automotive safety, arguing that we were at an inflection…
SpyCloud’s Identity Threat Protection solutions spearhead a holistic identity approach to security, illuminating correlated hidden identity exposures and facilitating fast,…
A new strain of Fully Undetectable (FUD) macOS malware, dubbed “Tiny FUD,” has emerged, showcasing sophisticated evasion techniques capable of…
Austin, TX, USA, February 4th, 2025, CyberNewsWire SpyCloud’s Identity Threat Protection solutions spearhead a holistic identity approach to security, illuminating…
Austin, TX, USA, February 4th, 2025, CyberNewsWire SpyCloud’s Identity Threat Protection solutions spearhead a holistic identity approach to security, illuminating…
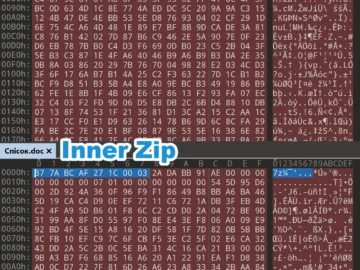
CVE-2025-0411, a Mark-of-the-Web bypass vulnerability in the open-source archiver tool 7-Zip that was fixed in November 2024, has been exploited…
Feb 04, 2025Ravie LakshmananVulnerability / Cyber Espionage A recently patched security vulnerability in the 7-Zip archiver tool was exploited in…
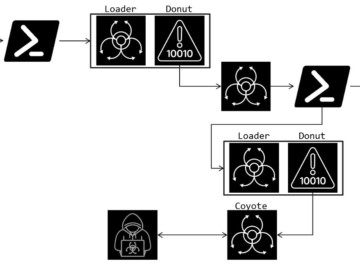
Coyote Banking Trojan targets Brazilian users, stealing data from 70+ financial apps and websites Pierluigi Paganini February 04, 2025 Coyote…