Linus Torvalds, the creator of the Linux kernel, has announced the release of Linux 6.14-rc1, marking the end of the…
Data and analytics leaders must build and address the adaptive and resilient data-driven business strategy and roadmap by improving the…
ParrotOS, the cybersecurity-focused Linux distribution, has recently released its latest update, Parrot 6.3, which includes a number of new features,…
Last week on Malwarebytes Labs: Last week on ThreatDown: Stay safe! Our business solutions remove all remnants of ransomware and…
The Justice Department made a new move in disrupting an international network of cybercriminals by announcing the coordinated seizure of…
BeyondTrust, a leading identity and access management firm, disclosed a critical security breach impacting 17 customers of its Remote Support…
Texas is the first state to ban DeepSeek on government devices Pierluigi Paganini February 03, 2025 Texas bans DeepSeek and…
A new threat to cybersecurity has emerged in the form of Devil-Traff, a bulk SMS platform designed to facilitate large-scale…
As organizations increasingly adopt Infrastructure as Code (IaC) to automate and manage their cloud environments, ensuring the security of these…
Authorities have successfully disrupted and dismantled the notorious online cybercrime marketplaces known as Cracked and Nulled, which had been operating…
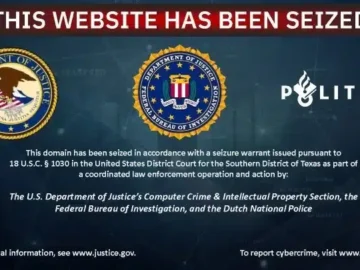
Law enforcement seized the domains of HeartSender cybercrime marketplaces Pierluigi Paganini February 03, 2025 U.S. and Dutch authorities seized 39…
As the digital world continues to evolve, so does the threat landscape, with cyberattacks growing more sophisticated and frequent. In…