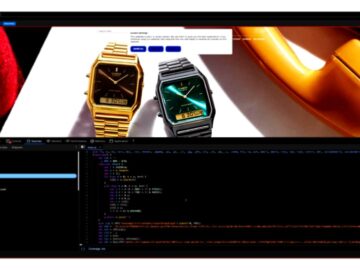
A recent investigation has revealed a significant web skimming campaign affecting at least 17 websites, including the UK site of…
The Cybersecurity Maturity Model Certification (CMMC) Program has been a headache for many defense contractors since the idea was first…
The rapid rise of DeepSeek, a Chinese generative AI platform, heightened concerns this week over the United States’ AI dominance…
Feb 01, 2025Ravie LakshmananCybercrime / Fraud Prevention U.S. and Dutch law enforcement agencies have announced that they have dismantled 39…
The notorious WantToCry ransomware group leverages misconfigured Server Message Block (SMB) services to infiltrate networks and launch widespread attacks. The…
Feb 01, 2025Ravie LakshmananVulnerability / Zero-Day BeyondTrust has revealed it completed an investigation into a recent cybersecurity incident that targeted…
The upcoming Netflix show Zero Day paints a dramatic picture of a disastrous cyberattack on the United States, with severe…
WhatsApp revealed on Friday that a “zero-click” spyware attack, attributed to the Israeli firm Paragon, has targeted scores of users…
Feb 01, 2025Ravie LakshmananPrivacy / Surveillance Meta-owned WhatsApp on Friday said it disrupted a campaign that involved the use of…
In a move to enhance user privacy, WhatsApp has rolled out a significant update allowing users to control who can…
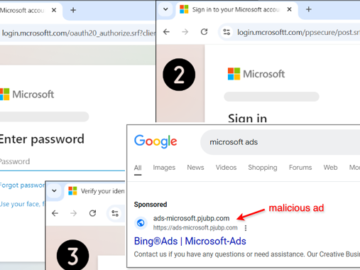
Feb 01, 2025Ravie LakshmananMalvertising / Mobile Security Cybersecurity researchers have discovered a malvertising campaign that’s targeting Microsoft advertisers with bogus…
Contec CMS8000 patient monitors contain a hidden backdoor Pierluigi Paganini February 01, 2025 The U.S. CISA and the FDA warned…