Philadelphia, Pennsylvania, January 7th, 2025, CyberNewsWire Security Risk Advisors today announced it has become a member of the Microsoft Intelligent…
Philadelphia, Pennsylvania, January 7th, 2025, CyberNewsWire Security Risk Advisors today announced it has become a member of the Microsoft Intelligent…
Jan 07, 2025Ravie LakshmananFirmware Security / Malware Cybersecurity researchers have uncovered firmware security vulnerabilities in the Illumina iSeq 100 DNA…
The recent attack campaign targeting browser extensions shows that malicious browser extensions are the next frontier for identity attacks. More…
A phishing campaign spoofing the United States Social Security Administration emerged in September 2024, delivering emails with embedded links to…
The United Nation’s International Civil Aviation Organization (ICAO) confirmed on Monday that it’s “actively investigating reports of a potential information…
Ramat Gan, Israel, January 7th, 2025, CyberNewsWire CyTwist, a leader in advanced next-generation threat detection solutions, has launched its patented…
Ramat Gan, Israel, January 7th, 2025, CyberNewsWire CyTwist, a leader in advanced next-generation threat detection solutions, has launched its patented…
Data science technology is about to revolutionize even the most traditional industries as it uses AI, Machine Learning, and Big Data,…
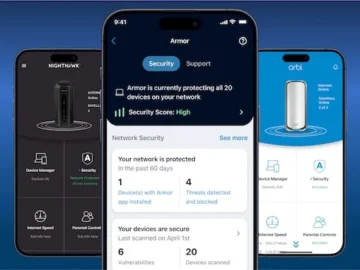
NETGEAR announced the next generation of NETGEAR Armor, powered by Bitdefender. As a subscription, Armor is a comprehensive cybersecurity service…
The Green Bay Packers American football team is notifying fans that a threat actor hacked its official online retail store…
It’s time once again to pay our respects to the once-famous cybersecurity solutions whose usefulness died in the past year….