Pure Storage thinks things are slotting into place for its predicted imminent demise of enterprise spinning disk. In December 2024,…
A critical authentication vulnerability in Fortinet’s FortiGate SSL VPN appliance tracked as CVE-2024-55591, has been weaponized in active attacks. Threat actors…
What if your face, fingerprint, or iris was your greatest vulnerability in a cyberattack? All those parts of you that…
Thank you for joining! Access your Pro+ Content below. 28 January 2025 Turbulent times ahead for tech Share this item…
Stepped-up SEC Enforcement Makes Proactive Security a Must The SEC’s finalized cybersecurity rules, effective starting mid-December 2023, place a spotlight…
You probably think of ransomware insurance as a safeguard against ransomware attacks and data loss – and it is, to…
Data Privacy Day (DPD), observed annually on January 28, is a global initiative dedicated to raising awareness about the critical…
Chinese AI platform DeepSeek faced a “large-scale” cyberattack Pierluigi Paganini January 28, 2025 Chinese AI company DeepSeek has disabled registrations…
The Akira ransomware group, a prominent player in the Ransomware-as-a-Service (RaaS) domain since March 2023, has intensified its operations with…
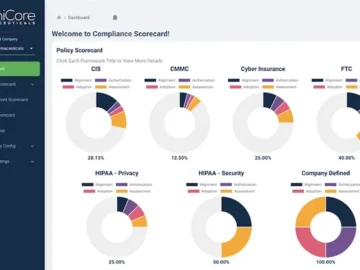
Compliance Scorecard released Compliance Scorecard Version 7. This latest release is designed to seamlessly integrate compliance into cybersecurity offerings, delivering…
I understand the importance of Zero Trust but, personally, I’ve had a hard time bridging the gap between how the…
A critical Insecure Direct Object Reference (IDOR) vulnerability has been identified in One Identity Manager, a widely used identity and…