Microsoft is not testing a fix for a longstanding known issue that is breaking SSH connections on some Windows 11…
Feb 20, 2025Ravie LakshmananCybercrime / Malware A malware campaign distributing the XLoader malware has been observed using the DLL side-loading…
A WIRED investigation into the inner workings of Google’s advertising ecosystem reveals that a wealth of sensitive information on Americans…
A joint advisory from the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information…
The payment card industry has set a critical deadline for businesses handling cardholder data or processing payments- by March 31,…
Microsoft fixed actively exploited flaw in Power Pages Pierluigi Paganini February 20, 2025 Microsoft addressed a privilege escalation vulnerability in…
The Digital Operational Resilience Act (DORA) is one of the most significant cybersecurity regulations for financial institutions in the European…
Most of us are familiar with the phrase ‘less is more,’ but when it comes to cybersecurity, sometimes, more can…
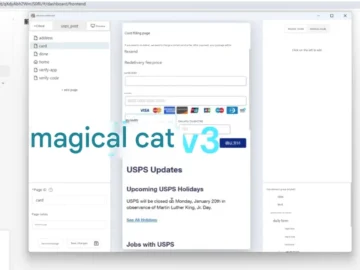
A new, improved version of Darcula, a cat-themed phishing-as-a-service (PhaaS) platform aimed at serving Chinese-speaking criminals, will be released this…
Feb 20, 2025Ravie LakshmananRansomware / Vulnerability A previously unknown threat activity cluster targeted European organizations, particularly those in the healthcare…
Cybersecurity is one of the most vital dimensions of contemporary existence with cloud storage, online transactions, and internet services ever…
Cloud Software Group released critical security updates to address a high-severity vulnerability in the NetScaler Console and NetScaler Console Agent,…