Learn more about bug bounty programs and how they work > The Growing Trend At HackerOne, we’ve observed a notable…
Jan 27, 2025Ravie LakshmananMalware / SEO Poisoning Threat hunters have detailed an ongoing campaign that leverages a malware loader called…
Efficiency and accuracy are crucial in vulnerability remediation. Yet, repetitive and manual handling of tasks throughout the vulnerability lifecycle remains…
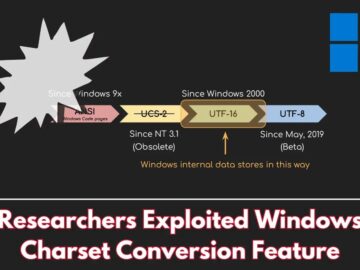
Researchers have exposed a systemic vulnerability within the Windows operating system, leveraging its “Best-Fit” charset conversion feature to bypass security…
Artificial Intelligence (AI) has the potential to revolutionize various sectors, but when leveraged by malicious actors, it can lead to…
PowerSchool has shared new updates to last week’s cyberattack that targeted the personal information of over 300,000 teachers. The PowerSchool…
Free Webinar – DevSecOps Hacks By embedding security into your CI/CD workflows, you can shift left, streamline your DevSecOps processes,…
The rise of deepfakes, artificial media that use AI to create hyper-realistic yet entirely fabricated images, videos, or audio, has…
The Challenge of Vulnerability Remediation When a vulnerability is identified, teams must determine the best approach to fixing it. This…
The Oligo Research team has disclosed a critical vulnerability in Meta’s widely used Llama-stack framework. This vulnerability, tracked as CVE-2024-50050, allows…
As I’m currently knee deep in testing agentic AI in all its forms, as well as new iterations of current…
This article showcases free, open-source cybersecurity tools that help you identify and address vulnerabilities, detect intrusion, protect websites from cyber…