UnitedHealth has revealed that 190 million Americans had their personal and healthcare data stolen in the Change Healthcare ransomware attack,…
In fact, the Cloud Security Alliance’s Top Threats to Cloud Computing 2024 Report ranks the following concerns as the top three:…
Remember the good old days of IT? Back when firewalls were like bouncers at a nightclub, and security was a…
Free Webinar – DevSecOps Hacks By embedding security into your CI/CD workflows, you can shift left, streamline your DevSecOps processes,…
Cary, North Carolina, January 26th, 2025, CyberNewsWire INE Security, a leading global provider of cybersecurity training and certifications, today announced…
Cary, North Carolina, January 26th, 2025, CyberNewsWire INE Security, a leading global provider of cybersecurity training and certifications, today announced…
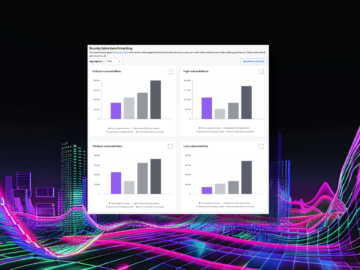
Without clear comparisons and long-term visibility, it’s challenging to identify areas for improvement and make informed, data-driven decisions. That’s why…
Artificial intelligence (AI) is making waves in many industries across the board. It found use in healthcare, manufacturing, retail, finance,…
Security researchers and election technology manufacturers at the Election Security Research Forum (ESRF). The Event In preparation for the election…
In this blog, we’ll explore who is and should be accountable for AI risk within organizations and how to empower…
A high-severity security flaw has been disclosed in Meta’s Llama large language model (LLM) framework that, if successfully exploited, could…
It sounds straightforward enough, but business logic vulnerabilities can result in an array of serious security issues, such as unauthorized…








![What Is a Business Logic Vulnerability? [Example] Hackerone logo](https://image.cybernoz.com/wp-content/uploads/2025/01/What-Is-a-Business-Logic-Vulnerability-Example-360x270.png)