Nearly six months ago, the Western media began to highlight growing concerns about potential Chinese interference in critical U.S. infrastructure….
Palo Alto Networks warns that a file read vulnerability (CVE-2025-0111) is now being chained in attacks with two other flaws…
Authored by the Publisher of Cyber Security Magazine Deep fake videos and audios – including phone calls from cyber criminals,…
Cary, North Carolina, February 19th, 2025, CyberNewsWire 2025 marks a time of unprecedented volatility in the technology job market. On…
Cary, North Carolina, February 19th, 2025, CyberNewsWire 2025 marks a time of unprecedented volatility in the technology job market. On…
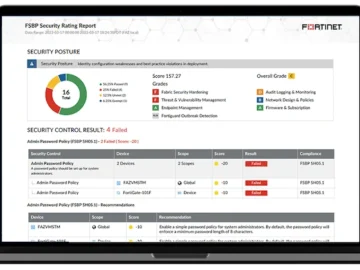
Fortinet announced significant enhancements to FortiAnalyzer, reinforcing its role in driving faster, smarter security operations (SecOps)—all from a single, turnkey…
Venture capital firm Insight Partners discloses security breach Pierluigi Paganini February 19, 2025 Venture capital firm Insight Partners suffered a…
Covid-19 has created a new urgency for cyber security solutions in Asia By Nora Cao Director of Cyber Security &…
Penetration testing has been shaping cybersecurity for decades—long before modern enterprises recognized its necessity. What started as a niche practice…
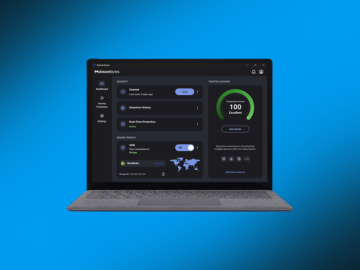
For the last four years, Malwarebytes has been protecting ARM-based machines running on Apple’s M-series processors. Now, we’ve expanded our…
ONE STEP ON, TWO STEPS BACK By Milica D. Djekic The media will frequently report that some kind of the…
Penetration testing has been shaping cybersecurity for decades—long before modern enterprises recognized its necessity. What started as a niche practice…