Oxylabs experts predict AI-driven web scraping, multi-agent systems, and evolving regulations will reshape industries and drive automation in 2025 The…
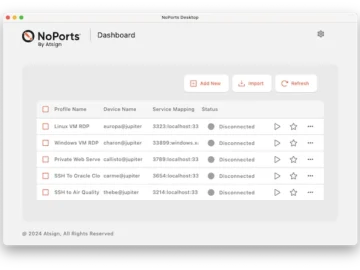
Atsign announced its new desktop client. This tool makes the protection of critical infrastructure easier by empowering people of all…
A new ransomware campaign has surfaced, leveraging Amazon Web Services’ (AWS) Server-Side Encryption with Customer Provided Keys (SSE-C) to encrypt…
In 2024, advancements in artificial intelligence (AI) have led to increasingly sophisticated threat actor exploits, such as deepfake technology used…
Artificial intelligence (AI) is transforming industries worldwide, offering startups powerful tools for innovation and growth. However, the same AI technologies…
From zero-day exploits to weaknesses in widely used software and hardware, the vulnerabilities uncovered last year underscore threat actors’ tactics…
In 2025, CISOs will have powerful new capabilities as generative artificial intelligence (GenAI) continues to mature. Evolving beyond providing answers…
In this Help Net Security interview, Nuno Martins da Silveira Teodoro, VP of Group Cybersecurity at Solaris, discusses the latest…
Application Security Engineer ENOC | UAE | On-site – View job details As an Application Security Engineer, you will establish…
Jan 14, 2025Ravie LakshmananVulnerability / Cybersecurity The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a second security…
Though many apply, only a few have the skills and patience to make it as a “watcher” an MI5 training…
Nominet, the official registry for .uk domain names and one of the largest country code registries globally has disclosed a…