CISA has tagged a command injection vulnerability (CVE-2024-12686) in BeyondTrust’s Privileged Remote Access (PRA) and Remote Support (RS) as actively…
The Cybersecurity and Infrastructure Security Agency (CISA) has updated its Known Exploited Vulnerabilities (KEV) Catalog with two new critical vulnerabilities,…
Optus has quietly paused the launch of its satellite-to-mobile service launch following its partnership with SpaceX’s Starlink. The Singtel-owned telco…
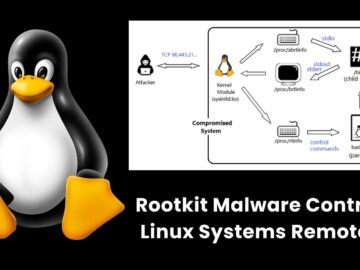
Fortinet researchers uncovered an advanced rootkit malware exploiting multiple zero-day vulnerabilities in enterprise appliances by executing a shell script (Install.sh)….
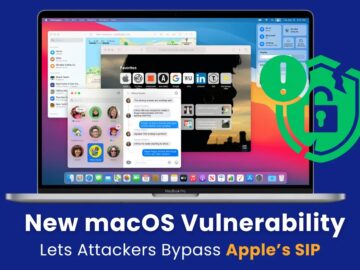
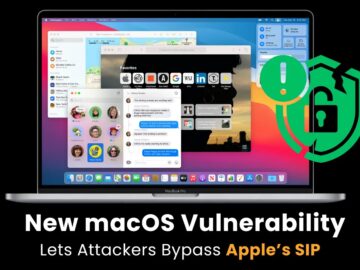
Microsoft Threat Intelligence has uncovered a critical macOS vulnerability that allowed attackers to bypass Apple’s System Integrity Protection (SIP). Known…
Smartphone shipments for Apple and Samsung declined in the fourth quarter globally, as they grapple with intense competition from Chinese…
Microsoft Threat Intelligence has identified a significant vulnerability in macOS that could allow attackers to bypass Apple’s System Integrity Protection…
Apple recently addressed a macOS vulnerability that allows attackers to bypass System Integrity Protection (SIP) and install malicious kernel drivers…
The hyperscale cloud providers – Amazon Web Service (AWS), Azure and Google Cloud Platform (CGP) – all offer a comprehensive…
Threat actors are exploiting a critical remote command execution vulnerability, tracked as CVE-2024-50603, in Aviatrix Controller instances to install backdoors…
The Cybersecurity and Infrastructure Security Agency (CISA) has added a critical OS command injection vulnerability (CVE-2024-12686) found in BeyondTrust’s Privileged…
Two separate announcements have highlighted the aggressive cost-cutting measures banks are putting in place as digital technologies replace thousands of…