Cybercriminals are executing sophisticated phishing attacks targeting Microsoft 365 users by employing deceptive URLs that closely resemble legitimate O365 domains,…
The Labour government has unveiled a 50-point plan to use artificial intelligence (AI) to help drive efficiency and growth across…
The U.S. Department of Justice (DoJ) has indicted three Russian nationals, Roman Vitalyevich Ostapenko, Alexander Evgenievich Oleynik, and Anton Vyachlavovich…
Any business that sells products or services in the European Union (EU) that use artificial intelligence (AI) must comply with…
Eindhoven University of Technology (TU/e) has been hit by a cyberattack, prompting the institution to suspend all lectures and educational…
The education and publishing giant Scholastic has fallen victim to a significant data breach affecting approximately 8 million people. The…
Last week on Malwarebytes Labs: Last week on ThreatDown: Stay safe! Our business solutions remove all remnants of ransomware and…
Ivanti has released patches to address two significant vulnerabilities in its Ivanti Connect Secure, Policy Secure, and ZTA Gateways products….
Cybersecurity is no longer just about protecting systems from external attackers. In an increasingly digitized world, the greatest risks often…
A proof-of-concept (PoC) exploit has been publicly disclosed for a critical vulnerability impacting macOS systems, identified as CVE-2024-54498. This vulnerability poses…
Microsoft took legal action against crooks who developed a tool to abuse its AI-based services Pierluigi Paganini January 13, 2025…
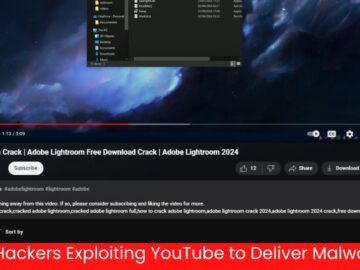
Cybercriminals are increasingly leveraging YouTube’s vast platform to distribute malware, bypassing traditional antivirus detections and exploiting users’ trust in the…