Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Ivanti Connect Secure zero-day exploited…
IBM disclosed a significant vulnerability in its watsonx.ai platform, potentially exposing users to cross-site scripting (XSS) attacks. The vulnerability, identified…
DoJ charged three Russian citizens with operating crypto-mixing services Pierluigi Paganini January 11, 2025 The U.S. Department of Justice charged…
The IRS relaunched its Identity Protection Personal Identification Number (IP PIN) program this week and all US taxpayers are encouraged to…
A deceptive proof-of-concept (PoC) exploit for CVE-2024-49113 (aka “LDAPNightmare”) on GitHub infects users with infostealer malware that exfiltrates sensitive data…
The surge in cyberattacks and the emerging role of Generative AI The importance of cyber security tools in protecting sensitive…
SUMMARY Phishing Scam Targets Job Seekers: Cybercriminals impersonate CrowdStrike recruiters to distribute cryptominer malware via fake job offers. Malware Delivery:…
SUMMARY Fake PoC Exploit for CVE-2024-49113: A malicious exploit, “LDAPNightmare,” targets researchers by disguising it as a PoC for a…
The Common Vulnerability Scoring System (CVSS) offers a standardized framework for characterizing and scoring vulnerabilities, helping the effort for vulnerability…
Email has a lot going for it. It’s quick, easy, and incredibly widely used. However, just like every other remote…
It’s dangerous out there. Cybersecurity threats are rampant and a system that doesn’t have adequate protection is a system that…
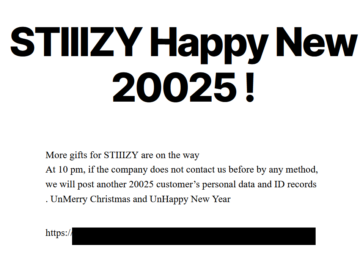
U.S. cannabis dispensary STIIIZY disclosed a data breach Pierluigi Paganini January 11, 2025 US marijuana dispensary STIIIZY warns customers of…