The UK Ministry of Defence (MoD) should embrace artificial intelligence (AI) to maintain its military advantages, which will require nurturing…
Cybercriminals are exploiting the recent critical LDAP vulnerabilities (CVE-2024-49112 and CVE-2024-49113) by distributing fake proof-of-concept exploits for CVE-2024-49113 (dubbed “LDAPNightmare”). …
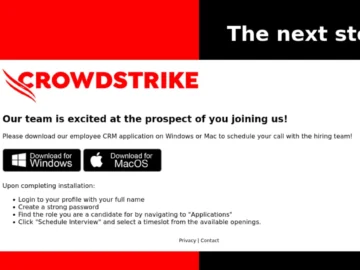
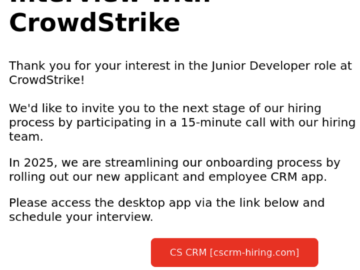
Cryptojackers are impersonating Crowdstrike via email to get developers to unwittingly install the XMRig cryptocurrency miner on their Windows PC,…
Jan 10, 2025Ravie LakshmananCryptomining / Malware Cybersecurity company CrowdStrike is alerting of a phishing campaign that exploits its own branding…
Investment in the UK fintech sector fell by 37% last year compared to 2023, but retained its leadership in Europe…
Samsung Mobile has announced the release of a comprehensive maintenance update as part of its monthly Security Maintenance Release (SMR)…
The QSC Loader service DLL named “loader.dll” leverages two distinct methods to obtain the path to the Core module code….
Jan 10, 2025Ravie LakshmananCyber Espionage / Cyber Attack Mongolia, Taiwan, Myanmar, Vietnam, and Cambodia have been targeted by the China-nexus…
Phishers abuse CrowdStrike brand targeting job seekers with cryptominer Pierluigi Paganini January 10, 2025 CrowdStrike warns of a phishing campaign…
A NonEuclid sophisticated C# Remote Access Trojan (RAT) designed for the.NET Framework 4.8 has been shown to pose a significant…
SUMMARY Banshee Stealer targets macOS users, distributed via fake GitHub repositories and phishing sites. The malware steals browser credentials, cryptocurrency…
Jan 10, 2025Ravie LakshmananCybersecurity / Android Cybersecurity researchers have detailed a now-patched security flaw impacting Monkey’s Audio (APE) decoder on…