Jan 13, 2025Ravie LakshmananVulnerability / Cloud Security A recently disclosed critical security flaw impacting the Aviatrix Controller cloud networking platform…
Personal data of nearly 100,000 individuals that have participated in trainings organized by CEPOL, the European Union (EU) Agency for…
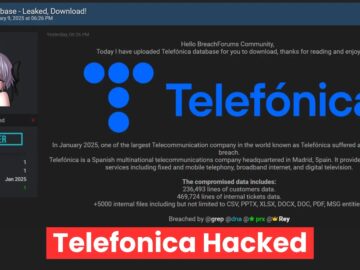
Spanish telecommunications giant Telefonica has confirmed a significant breach of its internal systems, with attackers claiming to have stolen approximately…
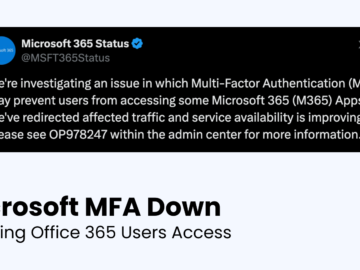
Microsoft has alerted users to an issue with its Multi-Factor Authentication (MFA) system, which has disrupted access to certain Microsoft…
In cybersecurity like in the emergency room, every moment is critical. Much like an emergency room, where nurses must quickly…
SUMMARY Indictment Filed: Three Russian nationals have been indicted for operating cryptocurrency mixers Blender.io and Sinbad.io, used to launder cybercrime…
A critical remote code execution (RCE) vulnerability, CVE-2024-50603, has been actively exploited in the wild, posing significant risks to cloud…
Ako, commonly referred to as MedusaReborn, is a C++-based ransomware strain that has been active since January 2020. It functions…
Microsoft has issued a warning regarding an ongoing issue with Multi-Factor Authentication (MFA) that is impacting some Microsoft 365 (M365)…
SUMMARY Telefonica confirmed a data breach involving its internal Jira ticketing system, with stolen data leaked online. Hackers used compromised…
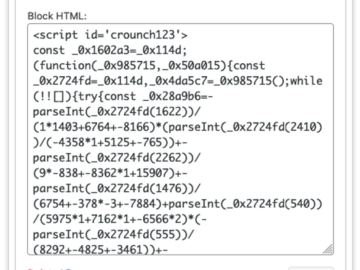
Credit Card Skimmer campaign targets WordPress via database injection Pierluigi Paganini January 13, 2025 Stealthy credit card skimmer targets WordPress…
Microsoft is investigating an ongoing Multi-Factor Authentication (MFA) outage that is blocking customers from accessing Microsoft 365 Office apps. Some affected…