A deceptive proof-of-concept (PoC) exploit for CVE-2024-49113 (aka “LDAPNightmare”) on GitHub infects users with infostealer malware that exfiltrates sensitive data…
The surge in cyberattacks and the emerging role of Generative AI The importance of cyber security tools in protecting sensitive…
SUMMARY Phishing Scam Targets Job Seekers: Cybercriminals impersonate CrowdStrike recruiters to distribute cryptominer malware via fake job offers. Malware Delivery:…
SUMMARY Fake PoC Exploit for CVE-2024-49113: A malicious exploit, “LDAPNightmare,” targets researchers by disguising it as a PoC for a…
The Common Vulnerability Scoring System (CVSS) offers a standardized framework for characterizing and scoring vulnerabilities, helping the effort for vulnerability…
Email has a lot going for it. It’s quick, easy, and incredibly widely used. However, just like every other remote…
It’s dangerous out there. Cybersecurity threats are rampant and a system that doesn’t have adequate protection is a system that…
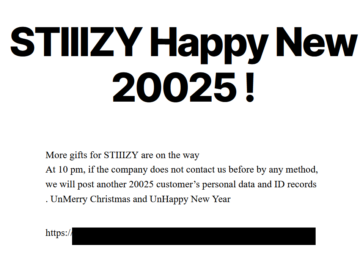
U.S. cannabis dispensary STIIIZY disclosed a data breach Pierluigi Paganini January 11, 2025 US marijuana dispensary STIIIZY warns customers of…
The stark reality is that cyberattacks are no longer distant threats. In 2024, they pose a real and immediate risk…
SUMMARY Infoblox discovered widespread domain spoofing in spam campaigns while investigating ‘Muddling Meerkat.’ Collaboration with the cybersecurity community linked Muddling…
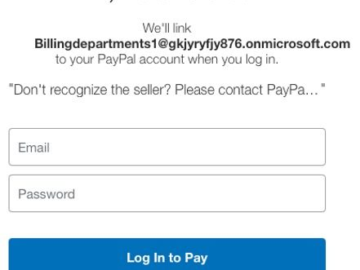
A novel PayPal phishing campaign hijacks accounts Pierluigi Paganini January 11, 2025 Fortinet warns of a phishing campaign using legitimate…
Jan 11, 2025Ravie LakshmananAI Security / Cybersecurity Microsoft has revealed that it’s pursuing legal action against a “foreign-based threat–actor group”…