The stark reality is that cyberattacks are no longer distant threats. In 2024, they pose a real and immediate risk…
SUMMARY Infoblox discovered widespread domain spoofing in spam campaigns while investigating ‘Muddling Meerkat.’ Collaboration with the cybersecurity community linked Muddling…
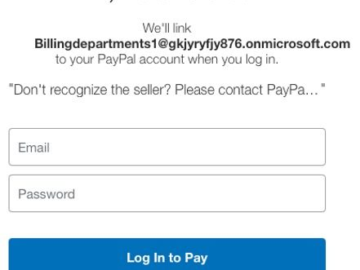
A novel PayPal phishing campaign hijacks accounts Pierluigi Paganini January 11, 2025 Fortinet warns of a phishing campaign using legitimate…
Jan 11, 2025Ravie LakshmananAI Security / Cybersecurity Microsoft has revealed that it’s pursuing legal action against a “foreign-based threat–actor group”…
Jan 11, 2025Ravie LakshmananFinancial Crime / Cryptocurrency The U.S. Department of Justice (DoJ) on Friday indicted three Russian nationals for…
A critical security vulnerability in Ivanti Connect Secure VPN appliances has left 2,048 instances worldwide exposed to potential exploitation, with…
Security researchers have successfully hacked Apple’s proprietary ACE3 USB-C controller. This chip, introduced with the iPhone 15 and iPhone 15…
A once tried-and-true security measure, passwords have failed to develop at a rate necessary to keep up with the vastness…
Heading into the new year, many businesses look at their budget, finding places where they can optimize their spending to…
Banshee macOS stealer supports new evasion mechanisms Pierluigi Paganini January 10, 2025 Experts found a new version of the Banshee…
SUMMARY Critical Vulnerabilities Identified: Ivanti has disclosed two critical vulnerabilities (CVE-2025-0282 and CVE-2025-0283) in Connect Secure, Policy Secure, and ZTA…
Spanish telecommunications company Telefónica confirms its internal ticketing system was breached after stolen data was leaked on a hacking forum….