TechRound, the voice of UK startups, reports that cybercrime will cost the world more than $10 trillion annually by 2025, according…
Jan 10, 2025Ravie LakshmananArtificial Intelligence / Cybercrime Cybersecurity researchers have shed light on a nascent artificial intelligence (AI) assisted ransomware…
Hyperscale datacentres are getting increasingly larger in size, as operators look to bolster the amount of IT load their facilities…
Fraudsters in the Middle East are exploiting a vulnerability in the government services portal. By impersonating government officials, they target…
Imagine walking into a board meeting with a tool that shows your board exactly how protected the organization is, based…
Cybersecurity reporting is a critical yet often overlooked opportunity for service providers managing cybersecurity for their clients, and specifically for…
The UK Ministry of Defence (MoD) should embrace artificial intelligence (AI) to maintain its military advantages, which will require nurturing…
Cybercriminals are exploiting the recent critical LDAP vulnerabilities (CVE-2024-49112 and CVE-2024-49113) by distributing fake proof-of-concept exploits for CVE-2024-49113 (dubbed “LDAPNightmare”). …
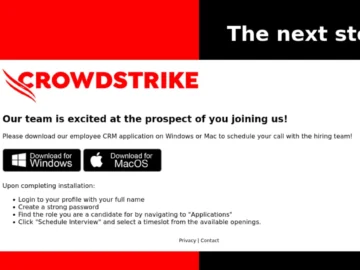
Cryptojackers are impersonating Crowdstrike via email to get developers to unwittingly install the XMRig cryptocurrency miner on their Windows PC,…
Jan 10, 2025Ravie LakshmananCryptomining / Malware Cybersecurity company CrowdStrike is alerting of a phishing campaign that exploits its own branding…
Investment in the UK fintech sector fell by 37% last year compared to 2023, but retained its leadership in Europe…
Samsung Mobile has announced the release of a comprehensive maintenance update as part of its monthly Security Maintenance Release (SMR)…