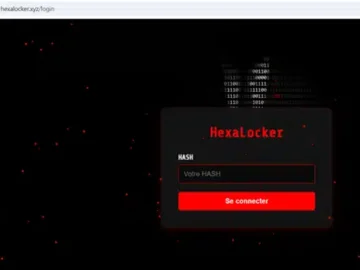
HexaLocker V2 has arrived on the market. This new version of the notorious HexaLocker ransomware has brought with it a…
Darktrace, a global leader in AI cybersecurity, has announced plans to acquire Cado Security, a UK-based cyber investigation and response…
India is witnessing a digital revolution, but along with it comes a daunting challenge—securing its massive digital infrastructure. With over…
China-linked APT group MirrorFace targets Japan Pierluigi Paganini January 10, 2025 Japanese authorities attributed a cyber-espionage campaign targeting the country…
Critical vulnerabilities in Ecovacs robot vacuums enable hackers to exploit these devices for surveillance and harassment. The findings, presented at…
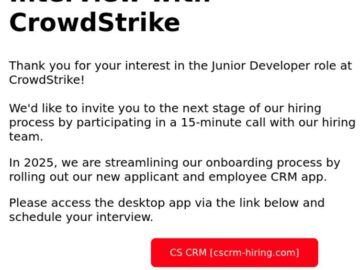
CrowdStrike, a leader in cybersecurity, uncovered a sophisticated phishing campaign that leverages its recruitment branding to propagate malware disguised as…
Cupertino, California, January 10, 2025—Cyble, a global leader in cybersecurity and threat intelligence, has once again solidified its dominance in…
Welcome to 2025 and a new year of patch excitement! In my December article, I talked about Microsoft’s Secure Future…
The BayMark Health Services, Inc. has reported a data breach to the California Attorney General, revealing that an unauthorized party…
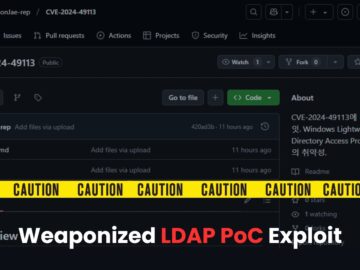
Security researchers are tricked into downloading and executing information-stealing malware by a fake proof-of-concept (PoC) exploit for CVE-2024-49113, dubbed LDAPNightmare….
In a sophisticated phishing campaign, uncovered cybercriminals are exploiting CrowdStrike’s recruitment branding to target developers and deploy the XMRig cryptominer….
Apple Inc. says its commitment to user privacy, emphasizing that its products, such as the digital assistant Siri, are designed…