The researchers exploited a novel attack vector by hijacking abandoned backdoors within other backdoors, which relied on expired or abandoned…
Torrance, United States / California, January 9th, 2025, CyberNewsWire Criminal IP, a globally recognized Cyber Threat Intelligence (CTI) solution by…
Microsoft has fixed a known issue causing the classic Outlook email client to stop responding when copying text with the…
The Green Bay Packers organization has disclosed a data breach affecting thousands of customers who made purchases on their official…
As we approach 2025, the cybersecurity landscape is continuing to evolve in response to an ever-changing array of threats and…
This article was researched and written by Stefan Dasic, manager, research and response for ThreatDown, powered by Malwarebytes Malwarebytes recently…
Jan 09, 2025Ravie Lakshmanan Cybersecurity researchers have uncovered a new, stealthier version of a macOS-focused information-stealing malware called Banshee Stealer….
Attackers have evolved a sophisticated social engineering scheme to target Middle Eastern banking consumers by posing as government officials and…
Every year brings new challenges — more threats, new techniques, more astute perpetrators, according to Rob Gurzeev, co-founder and CEO…
A critical vulnerability in Kerio Control, a popular firewall and Unified Threat Management (UTM) product, has been discovered that could…
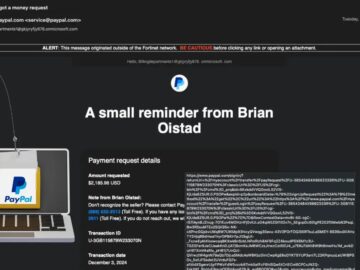
A new and sophisticated phishing scam has been uncovered, leveraging Microsoft 365 domains to trick users into compromising their PayPal…
SUMMARY Cybersecurity firm watchTowr discovered over 4,000 active hacker backdoors relying on expired domain names. These backdoors are pre-existing entry…