Did you know cybercrime could cost the world $10.5 trillion annually by 2025? It’s a staggering number and a wake-up…
Lumen reports that it has locked out the Salt Typhoon group from its network Pierluigi Paganini January 02, 2025 Lumen…
The year 2024 marked a pivotal moment in the ever-evolving realm of cybersecurity as cyberattacks became more frequent, sophisticated, and…
Cloud security researchers have uncovered alarming trends in identity compromises within Amazon Web Services (AWS) environments. Among the most prolific…
The Vulnerability in Focus The vulnerability, present in WPForms plugin versions 1.8.4 through 1.9.2.1, stems from a missing authorization check…
A sophisticated hacker group dubbed “EC2 Grouper” has been exploiting AWS tools and compromised credentials to launch attacks on cloud…
A 20-year-old U.S. Army soldier, Cameron John Wagenius, has been arrested and indicted by federal authorities for allegedly selling confidential…
The Cybersecurity and Infrastructure Security Agency (CISA) has expanded its Known Exploited Vulnerabilities (KEV) Catalog by adding a newly discovered…
D-Link warned users of several legacy router models about known vulnerabilities actively exploited by botnets. These devices, which have reached…
72% of security leaders agree that the age of AI necessitates a complete reset of how organizations approach application security,…
While the majority of employees avoid risky behaviors, a small subset makes them a habit, posing a significant cybersecurity challenge,…
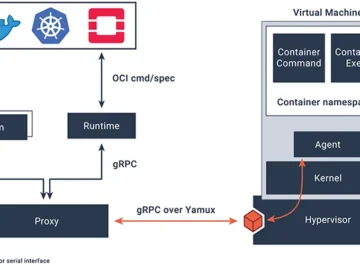
Kata Containers is an open-source project dedicated to creating a secure container runtime that combines the performance and simplicity of…