The cybersecurity landscape has witnessed a significant uptick in ransomware activity, with six new data-leak sites (DLSs) linked to emerging…
Feb 26, 2025Ravie LakshmananEnterprise Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday placed two security…
The UK government must “urgently” legislate on artificial intelligence (AI) given the clearly negative impacts it is already having on…
Critical infrastructure providers are under threat of more frequent and sophisticated attacks as state-linked threat groups are increasingly collaborating with…
Windows Active Directory (AD) service accounts are prime cyber-attack targets due to their elevated privileges and automated/continuous access to important…
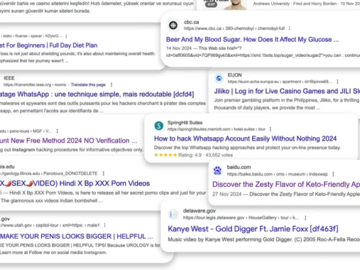
In a significant breakthrough, cybersecurity firm Silent Push has uncovered sensitive infrastructure tied to the Lazarus Group, a North Korean…
A cross-site scripting (XSS) vulnerability in a virtual tour framework has been weaponized by malicious actors to inject malicious scripts…
The use of internet of things (IoT) technology, combined with a software as a service (SaaS) platform, will help water…
Dive Brief: Global cybersecurity spending is projected to surge in coming years as artificial intelligence tools like chatbots and agents…
Forensic investigators have found that North Korean Lazarus hackers stole $1.5 billion from Bybit after hacking a developer’s device at…
A series of critical security vulnerabilities in the widely-used Rsync file synchronization tool have been uncovered, exposing millions of servers…
DalFox is an open-source tool for automating the detection of XSS vulnerabilities. With powerful testing capabilities and a wide range…