The Open Web Application Security Project has recently introduced a new Top 10 project – the Non-Human Identity (NHI) Top…
Google has released a critical update for the Chrome browser, addressing three high-severity security vulnerabilities. This patch, part of the…
Critical security flaw in SonicWall SMA 1000 appliances (CVE-2025-23006) exploited as a zero-day. Rated CVSS 9.8, patch immediately to protect…
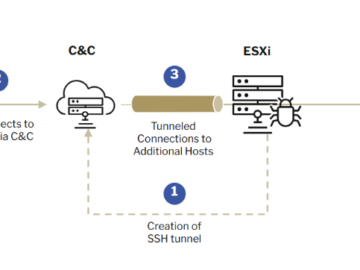
ESXi ransomware attacks use SSH tunnels to avoid detection Pierluigi Paganini January 27, 2025 Threat actors behind ESXi ransomware attacks…
In this interview, we explore Harley’s experience at DEFCON, the world’s largest hacker convention, where he took his skills to…
Researchers have identified a sophisticated phishing tactic leveraging Cloudflare’s workers.dev, a free domain name service, to execute credential theft campaigns….
The UK government’s decision to designate datacentres as critical national infrastructure (CNI) in September 2024 signalled its ambition to build…
Attackers allegedly stole $69 million from cryptocurrency platform Phemex Pierluigi Paganini January 27, 2025 Crooks stole at least $69 million…
Take Precision to the Next Level—Beyond Basic AI Efficiency and precision are critical in every operation. However, many security teams…
Jan 27, 2025Ravie LakshmananCyber Espionage / Threat Intelligence A previously unknown threat actor has been observed copying the tradecraft associated…
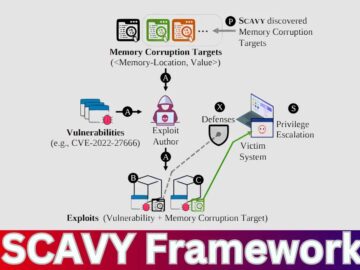
A breakthrough framework named SCAVY has been introduced to proactively detect memory corruption targets that could potentially lead to privilege escalation in…
Last week on Malwarebytes Labs: Last week on ThreatDown: Stay safe! Our business solutions remove all remnants of ransomware and…