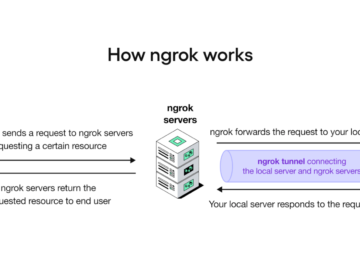
When gaining shell access to a machine on a network, a promising attack vector is to check the internal network…
Modern development and infrastructure management practices are fast paced and constantly evolving. In the race to innovate and expand, new…
The CRA will be a game-changing regulation for software and connected product security. The CRA imposes cybersecurity requirements for manufacturers…
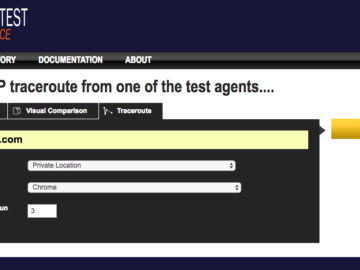
When Assetnote Continuous Security (CS) monitors your attack surface, one of the things it looks for are instances of WebPageTest….
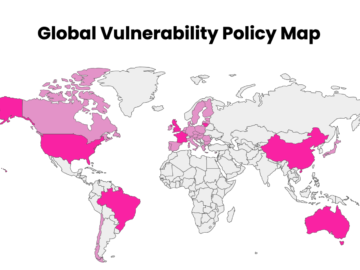
To help organizations keep up with the shifting landscape of VDP mandates and recommendations, HackerOne has developed the Global Vulnerability…
Motivations I recently made a video on how to find hidden files and folders on IIS through the use of…
The file upload vulnerability type is as broad in scope as the number of different file types. These vulnerabilities are…
Ransomware actors targeting ESXi bare metal hypervisors are leveraging SSH tunneling to persist on the system while remaining undetected. VMware…
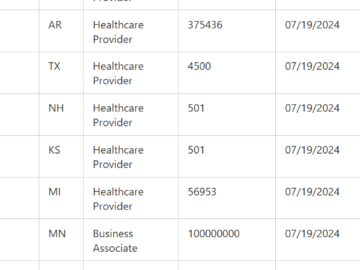
Change Healthcare data breach exposed the private data of over half the U.S. Pierluigi Paganini January 26, 2025 The Change…
What Is Cryptography? Cryptography is the practice and study of techniques for securing communication and information by transforming it into…
UnitedHealth has revealed that 190 million Americans had their personal and healthcare data stolen in the Change Healthcare ransomware attack,…
In fact, the Cloud Security Alliance’s Top Threats to Cloud Computing 2024 Report ranks the following concerns as the top three:…