The Python Package Index (PyPI) has announced the introduction of ‘Project Archival,’ a new system that allows publishers to archive…
OpenAI has introduced an innovative feature for ChatGPT called “Deep Research,” designed to handle complex, multi-step research tasks with exceptional…
In the ever-evolving landscape of cybercrime, bulk SMS platforms like Devil-Traff have emerged as powerful tools for phishing campaigns, exploiting…
A significant security vulnerability has been discovered in Alibaba Cloud Object Storage Service (OSS), enabling unauthorized users to upload data…
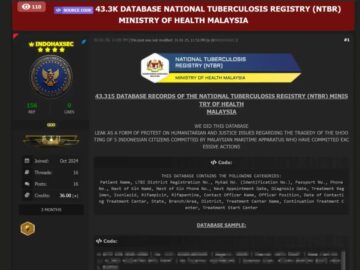
The Indonesian hacker group “INDOHAXSEC” has allegedly breached the National Tuberculosis Registry (NTBR) of Malaysia, managed by the Ministry of…
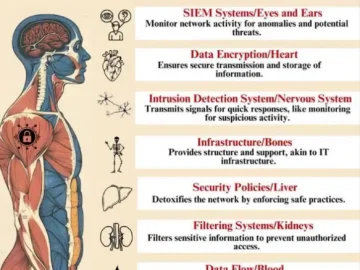
Understanding cybersecurity can sometimes feel like steering a maze of technical terms and complex systems. But a recent infographic shared…
The North Korean state-sponsored hacking group APT37 (aka ScarCruft, Reaper), has been identified leveraging group chat platforms to distribute malicious…
DeepSeek, the rapidly growing generative artificial intelligence (GenAI) model that made waves around the world at the end of January…
In war, as Sun Tzu taught us, the better you understand your enemy’s tactics (and yourself), the better equipped you…
Linus Torvalds, the creator of the Linux kernel, has announced the release of Linux 6.14-rc1, marking the end of the…
Data and analytics leaders must build and address the adaptive and resilient data-driven business strategy and roadmap by improving the…
ParrotOS, the cybersecurity-focused Linux distribution, has recently released its latest update, Parrot 6.3, which includes a number of new features,…