Subaru Starlink flaw allowed experts to remotely hack cars Pierluigi Paganini January 25, 2025 Subaru Starlink flaw exposed vehicles and…
This blog will break down the NIS2 Directive drawing information from the original directive briefing published by the European Parliament…
Retail and e-commerce organizations are major targets this time of year, which is why proactive security testing is essential to…
UnitedHealth Group has confirmed that a ransomware attack targeted its subsidiary, Change Healthcare, in February 2024, impacting 190 million Americans….
Participants in the Pwn2Own Automotive 2025 earned $886,250 Pierluigi Paganini January 25, 2025 The Pwn2Own Automotive 2025 hacking contest has…
1. Are You Prepared to Manage Incoming Vulnerability Reports? Naturally, the purpose of running a bug bounty program is to…
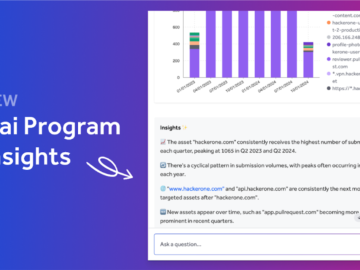
Transforming Security Program Management: A Day with Hai Picture this: It’s Monday morning, and your dashboard shows fifteen new vulnerability…
Dropbox, Microsoft, Okta – not only are these all major software companies, but each of them has fallen victim to…
Employees at HackerOne utilize the Working Genius model, which provides individuals and teams with a straightforward, practical, and effective framework…
Cybersecurity researchers discovered 270,000+ lines of American National Insurance customer data leaked online, potentially linked to the 2023 MOVEit breach….
The rapid development of artificial intelligence (AI) is fueling an increase in cyber-attacks, threatening the data infrastructure of businesses and…
When Saskia joined the tech world, she didn’t follow the conventional path of computer science degrees or coding boot camps….



![Is Your Security Ready For Bug Bounty? [5 Questions] Hackerone logo](https://cdn.cybernoz.com/wp-content/uploads/2025/01/Is-Your-Security-Ready-For-Bug-Bounty-5-Questions-360x270.png)