HackerOne has partnered with security and AI communities to advocate for stronger legal protections for independent researchers. Most recently, HackerOne…
U.S. CISA adds JQuery flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini January 23, 2025 U.S. Cybersecurity and Infrastructure…
Expanding Our Bug Bounty Program At Lightspark, we’ve always been focused on security that meets and exceeds industry standards. We’ve…
U.S. CISA adds SonicWall SMA1000 flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini January 24, 2025 U.S. Cybersecurity and…
Zyxel is warning that a bad security signature update is causing critical errors for USG FLEX or ATP Series firewalls, including putting…
What’s Needed for Secure by Design Success We spent years understanding the culprits of why “shift-left” controls fail to identify…
Microsoft has reminded Windows administrators that driver synchronization in Windows Server Update Services (WSUS) will be deprecated on April 18,…
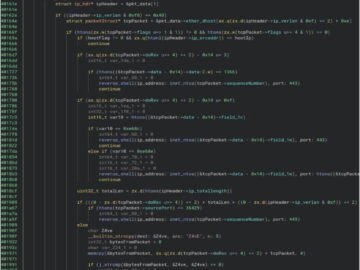
J-magic malware campaign targets Juniper routers Pierluigi Paganini January 24, 2025 Threat actors are targeting Juniper routers with a custom…
Facing the Reality: Cybersecurity’s Mounting Pressures The cybersecurity landscape is evolving at an unprecedented pace. This past year, breaches resulting…
The United States Department of Justice (DoJ) has announced the indictment of five men – two North Koreans, a Mexican…
A North Korean threat group has been using a technique called RID hijacking that tricks Windows into treating a low-privileged account…
US prosecutors charged five, including North Koreans, for tricking firms into hiring fake IT workers, sending $866K+ to fund weapons…