Hackers are distributing close to 1,000 web pages mimicking Reddit and the WeTransfer file sharing service that lead to downloading…
QNAP has fixed six rsync vulnerabilities that could let attackers gain remote code execution on unpatched Network Attached Storage (NAS)…
CISA and the FBI warned today that attackers are still exploiting Ivanti Cloud Service Appliances (CSA) security flaws patched since…
In the world of data protection, trust is everything. When faced with a disaster, ensuring your business continuity depends on…
Jan 23, 2025Ravie LakshmananMalware / Enterprise Security Enterprise-grade Juniper Networks routers have become the target of a custom backdoor as…
Brave Search has introduced a new feature called Rerank, which allows users to define search results ordering preferences and set…
The reliance on passwords as the cornerstone of digital authentication is slowly waning as organizations pivot towards more secure and…
A malicious campaign has been specifically targeting Juniper edge devices, many acting as VPN gateways, with malware dubbed J-magic that…
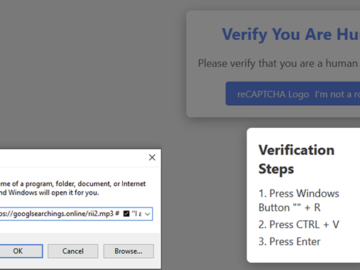
Jan 23, 2025Ravie LakshmananPhishing / Malware Cybersecurity researchers are calling attention to a new malware campaign that leverages fake CAPTCHA…
The Competition and Markets Authority (CMA) has begun an investigation of the Apple and Google mobile ecosystems. This is the…
SonicWall is warning about a pre-authentication deserialization vulnerability in SonicWall SMA1000 Appliance Management Console (AMC) and Central Management Console (CMC), with…
For some time, Cybersecurity Insiders have been alerting readers to the various cyber threats, such as ransomware, malware, crypto-mining software,…